Difference between revisions of "Cybersecurity Frameworks, Architectures & Roadmaps"
m |
m |
||
| (22 intermediate revisions by the same user not shown) | |||
| Line 18: | Line 18: | ||
* [[Cybersecurity]] ... [[Open-Source Intelligence - OSINT |OSINT]] ... [[Cybersecurity Frameworks, Architectures & Roadmaps | Frameworks]] ... [[Cybersecurity References|References]] ... [[Offense - Adversarial Threats/Attacks| Offense]] ... [[National Institute of Standards and Technology (NIST)|NIST]] ... [[U.S. Department of Homeland Security (DHS)| DHS]] ... [[Screening; Passenger, Luggage, & Cargo|Screening]] ... [[Law Enforcement]] ... [[Government Services|Government]] ... [[Defense]] ... [[Joint Capabilities Integration and Development System (JCIDS)#Cybersecurity & Acquisition Lifecycle Integration| Lifecycle Integration]] ... [[Cybersecurity Companies/Products|Products]] ... [[Cybersecurity: Evaluating & Selling|Evaluating]] | * [[Cybersecurity]] ... [[Open-Source Intelligence - OSINT |OSINT]] ... [[Cybersecurity Frameworks, Architectures & Roadmaps | Frameworks]] ... [[Cybersecurity References|References]] ... [[Offense - Adversarial Threats/Attacks| Offense]] ... [[National Institute of Standards and Technology (NIST)|NIST]] ... [[U.S. Department of Homeland Security (DHS)| DHS]] ... [[Screening; Passenger, Luggage, & Cargo|Screening]] ... [[Law Enforcement]] ... [[Government Services|Government]] ... [[Defense]] ... [[Joint Capabilities Integration and Development System (JCIDS)#Cybersecurity & Acquisition Lifecycle Integration| Lifecycle Integration]] ... [[Cybersecurity Companies/Products|Products]] ... [[Cybersecurity: Evaluating & Selling|Evaluating]] | ||
* [[Risk, Compliance and Regulation]] ... [[Ethics]] ... [[Privacy]] ... [[Law]] ... [[AI Governance]] ... [[AI Verification and Validation]] | * [[Risk, Compliance and Regulation]] ... [[Ethics]] ... [[Privacy]] ... [[Law]] ... [[AI Governance]] ... [[AI Verification and Validation]] | ||
| − | * [[ | + | * [[Telecommunications]] ... [[Computer Networks]] ... [[Telecommunications#5G|5G]] ... [[Satellite#Satellite Communications|Satellite Communications]] ... [[Quantum Communications]] ... [[Agents#Communication | Agents]] ... [[AI Generated Broadcast Content|AI Broadcast; Radio, Stream, TV]] |
| + | * [[Artificial General Intelligence (AGI) to Singularity]] ... [[Inside Out - Curious Optimistic Reasoning| Curious Reasoning]] ... [[Emergence]] ... [[Moonshots]] ... [[Explainable / Interpretable AI|Explainable AI]] ... [[Algorithm Administration#Automated Learning|Automated Learning]] | ||
* [[Libraries & Frameworks Overview]] ... [[Libraries & Frameworks]] ... [[Git - GitHub and GitLab]] ... [[Other Coding options]] | * [[Libraries & Frameworks Overview]] ... [[Libraries & Frameworks]] ... [[Git - GitHub and GitLab]] ... [[Other Coding options]] | ||
| + | * [[Development]] ... [[Notebooks]] ... [[Development#AI Pair Programming Tools|AI Pair Programming]] ... [[Codeless Options, Code Generators, Drag n' Drop|Codeless]] ... [[Hugging Face]] ... [[Algorithm Administration#AIOps/MLOps|AIOps/MLOps]] ... [[Platforms: AI/Machine Learning as a Service (AIaaS/MLaaS)|AIaaS/MLaaS]] | ||
| + | * [[Cybersecurity#MITRE ATT&CK™|MITRE ATT&CK™]] | ||
* [https://cyberexperts.com/cybersecurity-frameworks 23 Top Cybersecurity Frameworks | CyberExperts.com] | * [https://cyberexperts.com/cybersecurity-frameworks 23 Top Cybersecurity Frameworks | CyberExperts.com] | ||
* [https://www.cisecurity.org/insights/blog/align-to-a-framework-plan-a-cybersecurity-roadmaps-route Align to a Framework: Plan a Cybersecurity Roadmap's Route | CIS] | * [https://www.cisecurity.org/insights/blog/align-to-a-framework-plan-a-cybersecurity-roadmaps-route Align to a Framework: Plan a Cybersecurity Roadmap's Route | CIS] | ||
* [https://www.cisecurity.org/controls CIS Controls] | * [https://www.cisecurity.org/controls CIS Controls] | ||
* [https://www.cisecurity.org/blog/cis-cybersecurity-roadmap-for-small-businesses CIS Cybersecurity Roadmap] | * [https://www.cisecurity.org/blog/cis-cybersecurity-roadmap-for-small-businesses CIS Cybersecurity Roadmap] | ||
| − | * [https://www.fedramp.gov/ NIST FedRAMP] security for the cloud | + | * [https://www.fedramp.gov/ NIST FedRAMP|] [[National Institute of Standards and Technology (NIST)|NIST]] ... security for the cloud |
| − | * [https://www.nist.gov/cyberframework NIST Cybersecurity Framework] - consists of standards, guidelines, and best practices to manage cybersecurity-related risk. | + | * [https://www.nist.gov/cyberframework NIST Cybersecurity Framework|] [[National Institute of Standards and Technology (NIST)|NIST]] - consists of standards, guidelines, and best practices to manage cybersecurity-related risk. |
| − | * [https://www.nist.gov/cyberframework/online-learning/introduction-framework-roadmap Introduction to the Framework Roadmap | NIST] | + | * [https://www.nist.gov/cyberframework/online-learning/introduction-framework-roadmap Introduction to the Framework Roadmap |] [[National Institute of Standards and Technology (NIST)|NIST]] |
| − | * [https://csrc.nist.gov/Projects/Cryptographic-Module-Validation-Program/Standards FIPS 140-2 Security Requirements for Cryptographic Modules] | + | * [https://csrc.nist.gov/Projects/Cryptographic-Module-Validation-Program/Standards FIPS 140-2 Security Requirements for Cryptographic Modules|] [[National Institute of Standards and Technology (NIST)|NIST]]] |
* [https://www.iso.org/isoiec-27001-information-security.html ISO/IEC 27001] | * [https://www.iso.org/isoiec-27001-information-security.html ISO/IEC 27001] | ||
* [https://www.iso.org/standard/50341.html ISO/IEC 15408-1 ISO/IEC Information Technology Task Force (ITTF)] | * [https://www.iso.org/standard/50341.html ISO/IEC 15408-1 ISO/IEC Information Technology Task Force (ITTF)] | ||
* [https://sabsa.org SABSA] | * [https://sabsa.org SABSA] | ||
* [https://pubs.opengroup.org/architecture/togaf9-doc/arch TOGAF] | * [https://pubs.opengroup.org/architecture/togaf9-doc/arch TOGAF] | ||
| − | * [https://learn.microsoft.com/en-us/security/cybersecurity-reference-architecture/mcra Microsoft Cybersecurity Reference Architectures] | + | * [https://learn.microsoft.com/en-us/security/cybersecurity-reference-architecture/mcra Microsoft Cybersecurity Reference Architectures|] [[Microsoft]] |
| − | * [https://learn.microsoft.com/en-us/security/cybersecurity-reference-architecture/zero-trust-rapid-modernization-plan Zero Trust Rapid Modernization Plan] | + | * [https://learn.microsoft.com/en-us/security/cybersecurity-reference-architecture/zero-trust-rapid-modernization-plan Zero Trust Rapid Modernization Plan|] [[Microsoft]] |
| − | * [https://mva.microsoft.com/en-US/training-courses/cybersecurity-reference-architecture-17632?l=sa3b33xtD_404300474 Cybersecurity Reference Architecture | Microsoft] | + | * [https://mva.microsoft.com/en-US/training-courses/cybersecurity-reference-architecture-17632?l=sa3b33xtD_404300474 Cybersecurity Reference Architecture |] [[Microsoft]] |
| − | * [https://learn.microsoft.com/en-us/security/cybersecurity-reference-architecture/mcra Microsoft Cybersecurity Reference Architectures - Security | Microsoft] | + | * [https://learn.microsoft.com/en-us/security/cybersecurity-reference-architecture/mcra Microsoft Cybersecurity Reference Architectures - Security |] [[Microsoft]] |
* [https://www.us-cert.gov/ United States Computer Emergency Readiness Team (US-CERT)] | * [https://www.us-cert.gov/ United States Computer Emergency Readiness Team (US-CERT)] | ||
* [https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=cti OASIS Cyber Threat Intelligence (CTI) TC] [https://openc2.org/ OpenC2] | * [https://www.oasis-open.org/committees/tc_home.php?wg_abbrev=cti OASIS Cyber Threat Intelligence (CTI) TC] [https://openc2.org/ OpenC2] | ||
| − | * [https://www.dhs.gov/using-cybersecurity-framework Using the Cybersecurity Framework | DHS] | + | * [https://www.dhs.gov/using-cybersecurity-framework Using the Cybersecurity Framework |] [[U.S. Department of Homeland Security (DHS)| DHS]] |
* [https://securityintelligence.com/how-stix-taxii-and-cybox-can-help-with-standardizing-threat-information/ How STIX, TAXII and CybOX Can Help With Standardizing Threat Information] | * [https://securityintelligence.com/how-stix-taxii-and-cybox-can-help-with-standardizing-threat-information/ How STIX, TAXII and CybOX Can Help With Standardizing Threat Information] | ||
| Line 45: | Line 48: | ||
= Important Tools = | = Important Tools = | ||
| + | |||
Cybersecurity frameworks, architectures and roadmaps are important tools for organizations to improve their security posture and manage cyber risks. Here is some information about them from various sources: | Cybersecurity frameworks, architectures and roadmaps are important tools for organizations to improve their security posture and manage cyber risks. Here is some information about them from various sources: | ||
| Line 60: | Line 64: | ||
* <b>NIST Cybersecurity Framework (CSF)</b>: A voluntary framework developed by the National Institute of Standards and Technology (NIST) for critical infrastructure sectors in the US, but widely adopted by other sectors and countries as well. The CSF consists of five core functions: Identify, Protect, Detect, Respond and Recover. Each function has a set of categories, subcategories and informative references that provide guidance on specific security outcomes. | * <b>NIST Cybersecurity Framework (CSF)</b>: A voluntary framework developed by the National Institute of Standards and Technology (NIST) for critical infrastructure sectors in the US, but widely adopted by other sectors and countries as well. The CSF consists of five core functions: Identify, Protect, Detect, Respond and Recover. Each function has a set of categories, subcategories and informative references that provide guidance on specific security outcomes. | ||
| + | ** [https://csrc.nist.gov/Projects/Cybersecurity-Framework/Filters#/csf/filters NIST Cybersecurity Framework 2.0 Reference Tool | NIST] ... allows users to explore the Draft CSF 2.0 Core (Functions, Categories, Subcategories, Implementation Examples) and offers human and machine-readable versions of the draft Core (in both JSON and Excel formats). Currently, the tool allows users to view and export portions of the Core using key search terms. This tool will ultimately enable users to create their own version of the CSF 2.0 Core with selected Informative References and will provide a simple and streamlined way for users to explore different aspects of the CSF Core. | ||
* <b>ISO/IEC 27001</b>: An international standard for information security management systems (ISMS) that specifies the requirements for establishing, implementing, maintaining and improving an ISMS. The standard covers all aspects of information security, including risk assessment, policies, procedures, controls, monitoring, auditing and improvement. The standard also provides a certification scheme for organizations that want to demonstrate their compliance. | * <b>ISO/IEC 27001</b>: An international standard for information security management systems (ISMS) that specifies the requirements for establishing, implementing, maintaining and improving an ISMS. The standard covers all aspects of information security, including risk assessment, policies, procedures, controls, monitoring, auditing and improvement. The standard also provides a certification scheme for organizations that want to demonstrate their compliance. | ||
* <b>CIS Controls</b>: A set of 20 prioritized and actionable security controls developed by the Center for Internet Security (CIS) based on the most common and effective practices observed in real-world incidents. The CIS Controls cover both technical and organizational aspects of security, such as inventory, configuration, vulnerability management, access control, incident response and awareness training. The CIS Controls also provide implementation guidance for different types of organizations, such as small businesses, enterprises and cloud environments. | * <b>CIS Controls</b>: A set of 20 prioritized and actionable security controls developed by the Center for Internet Security (CIS) based on the most common and effective practices observed in real-world incidents. The CIS Controls cover both technical and organizational aspects of security, such as inventory, configuration, vulnerability management, access control, incident response and awareness training. The CIS Controls also provide implementation guidance for different types of organizations, such as small businesses, enterprises and cloud environments. | ||
| Line 78: | Line 83: | ||
* <b>Microsoft Cybersecurity Reference Architectures (MCRA)</b>: A set of detailed technical diagrams that describe Microsoft's cybersecurity capabilities and how they integrate with Microsoft platforms and third-party platforms, such as Microsoft 365, Azure, ServiceNow, Salesforce, AWS and GCP. The MCRA covers various topics such as zero trust user access, security operations, operational technology (OT), multi-cloud and cross-platform capabilities, attack chain coverage, Azure native security controls and security organizational functions. | * <b>Microsoft Cybersecurity Reference Architectures (MCRA)</b>: A set of detailed technical diagrams that describe Microsoft's cybersecurity capabilities and how they integrate with Microsoft platforms and third-party platforms, such as Microsoft 365, Azure, ServiceNow, Salesforce, AWS and GCP. The MCRA covers various topics such as zero trust user access, security operations, operational technology (OT), multi-cloud and cross-platform capabilities, attack chain coverage, Azure native security controls and security organizational functions. | ||
* <b>SABSA</b>: A framework and methodology for developing business-driven, risk-based and architecture-led security solutions. SABSA stands for Sherwood Applied Business Security Architecture. The framework consists of six layers: contextual (business), conceptual (architecture), logical (design), physical (implementation), component (build) and operational (management). Each layer has a set of attributes that define the security requirements, objectives, functions, services, components and metrics. | * <b>SABSA</b>: A framework and methodology for developing business-driven, risk-based and architecture-led security solutions. SABSA stands for Sherwood Applied Business Security Architecture. The framework consists of six layers: contextual (business), conceptual (architecture), logical (design), physical (implementation), component (build) and operational (management). Each layer has a set of attributes that define the security requirements, objectives, functions, services, components and metrics. | ||
| − | * <b>TOGAF</b>: A framework for enterprise architecture that provides a comprehensive approach to planning, designing, implementing and governing an organization's information technology. TOGAF stands for The Open Group Architecture Framework. The framework consists of four domains: business (strategy), data (information), application (system) and technology (infrastructure). Each domain has a set of principles, standards, models and views that guide the architecture development process. | + | * <b>TOGAF</b>: A framework for enterprise architecture that provides a comprehensive approach to planning, designing, implementing and governing an organization's information technology. TOGAF stands for The Open Group Architecture Framework. The framework consists of four domains: business (strategy), data (information), application (system) and technology (infrastructure). Each domain has a set of principles, standards, models and views that guide the architecture [[development]] process. |
<b>Cybersecurity Roadmaps</b> | <b>Cybersecurity Roadmaps</b> | ||
| Line 92: | Line 97: | ||
Some examples of cybersecurity roadmaps are: | Some examples of cybersecurity roadmaps are: | ||
| − | * <b>NIST Cybersecurity Framework Roadmap</b>: A companion document to the NIST CSF that identifies key activities planned for improving and enhancing the CSF. The roadmap is not exhaustive in describing all planned activities within NIST but focuses on high-priority areas for development, alignment and collaboration. The roadmap version 1.1 identifies 14 areas such as confidence mechanisms, cyberattack lifecycle, cybersecurity workforce, cyber supply chain risk management, federal agency cybersecurity alignment, governance and enterprise risk management etc. | + | * <b>NIST Cybersecurity Framework Roadmap</b>: A companion document to the NIST CSF that identifies key activities planned for improving and enhancing the CSF. The roadmap is not exhaustive in describing all planned activities within NIST but focuses on high-priority areas for [[development]], alignment and collaboration. The roadmap version 1.1 identifies 14 areas such as confidence mechanisms, cyberattack lifecycle, cybersecurity workforce, cyber supply chain risk management, federal agency cybersecurity alignment, governance and enterprise risk management etc. |
| − | * <b>Zero Trust Rapid Modernization Plan (RaMP)</b>: A part of the MCRA that provides a practical and actionable approach to implementing zero trust principles and practices in an organization. The RaMP consists of four phases: assess, plan, execute and optimize. Each phase has a set of steps, activities and deliverables that help organizations to define their zero trust vision, identify their current state and gaps, prioritize and implement zero trust capabilities and measure and improve their zero trust maturity. | + | * <b>[[Cybersecurity Frameworks, Architectures & Roadmaps#Zero Trust|Zero Trust]] Rapid Modernization Plan (RaMP)</b>: A part of the MCRA that provides a practical and actionable approach to implementing zero trust principles and practices in an organization. The RaMP consists of four phases: assess, plan, execute and optimize. Each phase has a set of steps, activities and deliverables that help organizations to define their zero trust vision, identify their current state and gaps, prioritize and implement zero trust capabilities and measure and improve their zero trust maturity. |
* <b>CIS Cybersecurity Roadmap</b>: A guide for small and medium-sized businesses (SMBs) to improve their cybersecurity posture using the CIS Controls. The roadmap provides a simple and practical way to implement the CIS Controls based on three levels of security maturity: basic, foundational and organizational. The roadmap also provides tips, resources and tools to help SMBs with their security journey. | * <b>CIS Cybersecurity Roadmap</b>: A guide for small and medium-sized businesses (SMBs) to improve their cybersecurity posture using the CIS Controls. The roadmap provides a simple and practical way to implement the CIS Controls based on three levels of security maturity: basic, foundational and organizational. The roadmap also provides tips, resources and tools to help SMBs with their security journey. | ||
| Line 109: | Line 114: | ||
{| class="wikitable" style="width: 550px;" | {| class="wikitable" style="width: 550px;" | ||
|| | || | ||
| − | <youtube> | + | <youtube>I49iK8AzU2I</youtube> |
| − | <b> | + | <b>DEVNET 1158 - Cognitive Threat Analytics - Behavioral Breach Detection via TAXII/STIX API |
| − | </b><br> | + | </b><br>Speaker: Petr Cernohorsky. Introducing Cognitive Threat Analytics (CTA), Cisco's automated breach detection technology based on statistical modeling and machine learning of network traffic behaviors, whose goal is to identify end-user devices within the monitored network that from network perspective do not represent a [[Agents#Communication | communication]] of a legitimate human user behind their web browser, but actually represent a malware-infected (breached) device establishing its command & control [[Agents#Communication | communication]] to an external malicious infrastructure. The CTA technology produces actionable security intelligence for security operations and threat research to act on. The STIX/TAXII API standards are being used for the security intelligence interchange. An integration is available with the leading SIEM vendors and other STIX/TAXII compliant clients. For all the DevNet Zone 2015 San Diego |
|} | |} | ||
|}<!-- B --> | |}<!-- B --> | ||
| Line 146: | Line 151: | ||
<b>ISMS [ ISO 27001 ] | INFORMATION SECURITY POLICY - How to Write | <b>ISMS [ ISO 27001 ] | INFORMATION SECURITY POLICY - How to Write | ||
</b><br>ISMS [ ISO 27001 ] - How to write Information Security Policy | </b><br>ISMS [ ISO 27001 ] - How to write Information Security Policy | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
|} | |} | ||
|}<!-- B --> | |}<!-- B --> | ||
| Line 172: | Line 160: | ||
{| class="wikitable" style="width: 550px;" | {| class="wikitable" style="width: 550px;" | ||
|| | || | ||
| − | <youtube> | + | <youtube>xaR6Btxh6jE</youtube> |
<b>Trusted Internet Connections (TIC) 3 Webinar | <b>Trusted Internet Connections (TIC) 3 Webinar | ||
</b><br>In this webinar, Jim Russo of GSA's Office of Information Technology Category and Sean Connelly of the Cybersecurity And Infrastructure Security Agency break down the Office of Management and Budget's Trusted Internet Connections (TIC) 3.0 guidance. Learn how agencies can adopt popular cloud models while still meeting security standards. Visit https://www.cisa.gov/trusted-internet... to learn more. www.gsa.gov | </b><br>In this webinar, Jim Russo of GSA's Office of Information Technology Category and Sean Connelly of the Cybersecurity And Infrastructure Security Agency break down the Office of Management and Budget's Trusted Internet Connections (TIC) 3.0 guidance. Learn how agencies can adopt popular cloud models while still meeting security standards. Visit https://www.cisa.gov/trusted-internet... to learn more. www.gsa.gov | ||
| Line 185: | Line 173: | ||
|} | |} | ||
|}<!-- B --> | |}<!-- B --> | ||
| − | + | ||
| − | = Zero Trust = | + | = <span id="Zero Trust"></span>Zero Trust = |
| + | [https://www.youtube.com/results?search_query=ai+zero+trust+zta+cybersecurity YouTube] | ||
| + | [https://www.quora.com/search?q=ai%20zero%20trust%20zta%20cybersecurity ... Quora] | ||
| + | [https://www.google.com/search?q=ai+zero+trust+zta+cybersecurity ...Google search] | ||
| + | [https://news.google.com/search?q=ai+zero+trust+zta+cybersecurity ...Google News] | ||
| + | [https://www.bing.com/news/search?q=ai+zero+trust+zta+cybersecurity&qft=interval%3d%228%22 ...Bing News] | ||
| + | |||
| + | * [[Perspective]] ... [[Context]] ... [[In-Context Learning (ICL)]] ... [[Transfer Learning]] ... [[Out-of-Distribution (OOD) Generalization]] | ||
| + | * [[Causation vs. Correlation]] ... [[Autocorrelation]] ...[[Convolution vs. Cross-Correlation (Autocorrelation)]] | ||
| + | * [[Policy]] ... [[Policy vs Plan]] ... [[Constitutional AI]] ... [[Trust Region Policy Optimization (TRPO)]] ... [[Policy Gradient (PG)]] ... [[Proximal Policy Optimization (PPO)]] | ||
| + | * [[Architectures]] for AI ... [[Enterprise Architecture (EA)]] ... [[Enterprise Portfolio Management (EPM)]] ... [[Architecture and Interior Design]] | ||
| + | * [[Immersive Reality]] ... [[Metaverse]] ... [[Omniverse]] ... [[Transhumanism]] ... [[Religion]] | ||
| + | * [[Telecommunications]] ... [[Computer Networks]] ... [[Telecommunications#5G|5G]] ... [[Satellite#Satellite Communications|Satellite Communications]] ... [[Quantum Communications]] ... [[Agents#Communication | Communication Agents]] ... [[Smart Cities]] ... [[Digital Twin]] ... [[Internet of Things (IoT)]] | ||
| + | * [[Risk, Compliance and Regulation]] ... [[Ethics]] ... [[Privacy]] ... [[Law]] ... [[AI Governance]] ... [[AI Verification and Validation]] | ||
| + | * [[Cybersecurity]] ... [[Open-Source Intelligence - OSINT |OSINT]] ... [[Cybersecurity Frameworks, Architectures & Roadmaps | Frameworks]] ... [[Cybersecurity References|References]] ... [[Offense - Adversarial Threats/Attacks| Offense]] ... [[National Institute of Standards and Technology (NIST)|NIST]] ... [[U.S. Department of Homeland Security (DHS)| DHS]] ... [[Screening; Passenger, Luggage, & Cargo|Screening]] ... [[Law Enforcement]] ... [[Government Services|Government]] ... [[Defense]] ... [[Joint Capabilities Integration and Development System (JCIDS)#Cybersecurity & Acquisition Lifecycle Integration| Lifecycle Integration]] ... [[Cybersecurity Companies/Products|Products]] ... [[Cybersecurity: Evaluating & Selling|Evaluating]] | ||
| + | * [https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf Zero Trust Architecture | NIST] | ||
| + | * [https://learn.microsoft.com/en-us/azure/architecture/guide/security/conditional-access-design Conditional Access design principles and dependencies | Microsoft] | ||
| + | * [https://en.wikipedia.org/wiki/Zero_trust_security_model Zero trust security model | Wikipedia] | ||
| + | |||
| + | Zero Trust architecture is a cybersecurity approach that assumes breaches will occur and uses risk-based access controls to limit the damage from an attack. Instead of only guarding an organization’s perimeter, Zero Trust architecture protects each file, email, and network by authenticating every identity and device. Rather than just securing one network, Zero Trust architecture also helps secure remote access, personal devices, and third-party apps. The principles of Zero Trust are: Verify explicitly, Use least privileged access, Assume breach and Require end-to-end encryption. | ||
| + | |||
| + | |||
| + | <hr><center><b><i> | ||
| + | |||
| + | Never trust, always verify | ||
| + | |||
| + | </i></b></center><hr> | ||
| + | |||
| + | |||
| + | Part of... [[Telecommunications#Software-Defined Networking (SDN)|software-defined networking (SD-WAN)]] and Secure Access Service Edge (SASE). SASE delivers wide-area networking with [[cybersecurity]] both on-site and in the cloud as DoD expands its reliance on cloud data storage. One of the key tenants of zero trust involves identity. Thunderdome will use identity verification, including public key infrastructure (PKI), which uses a certificate to validate data being sent from one point to another, and identity credentialing and access management (ICAM). ICAM verifies a person’s identity and links them to their allowed access privileges. - [https://federalnewsnetwork.com/defense-news/2023/02/thunderdome-hits-its-targets-disa-moves-to-next-phase-of-zero-trust/ Thunderdome hits its targets, DISA moves to next phase of zero trust | Alexandra Lohr - Federal New Network] | ||
| + | |||
| + | * [[Telecommunications#Software-Defined Networking (SDN)|Software-defined networking (SD-WAN)]] | ||
| + | * [https://www.cisco.com/c/en/us/products/security/what-is-sase-secure-access-service-edge.html What Is Secure Access Service Edge (SASE)? | CISCO] ... a network architecture that combines VPN and SD-WAN capabilities with cloud-native security functions such as secure web gateways, cloud access security brokers, firewalls, and zero-trust network access. These functions are delivered from the cloud and provided as a service by the SASE vendor. | ||
| + | * [https://www.cisa.gov/identity-credential-and-access-management-icam Identity credentialing and access management (ICAM)] ... ensure that the right person with the right privileges can access the right information at the right time | ||
| + | * [https://breakingdefense.com/2023/03/disa-completes-thunderdome-prototype-a-step-closer-to-achieving-dods-zero-trust-vision/ Thunderdome is a network architecture program; laying a zero-trust technology foundation] | ||
| + | * [[Defense#US Defense Information Systems Agency (DISA)|US Defense Information Systems Agency (DISA)]] | ||
| + | |||
| + | |||
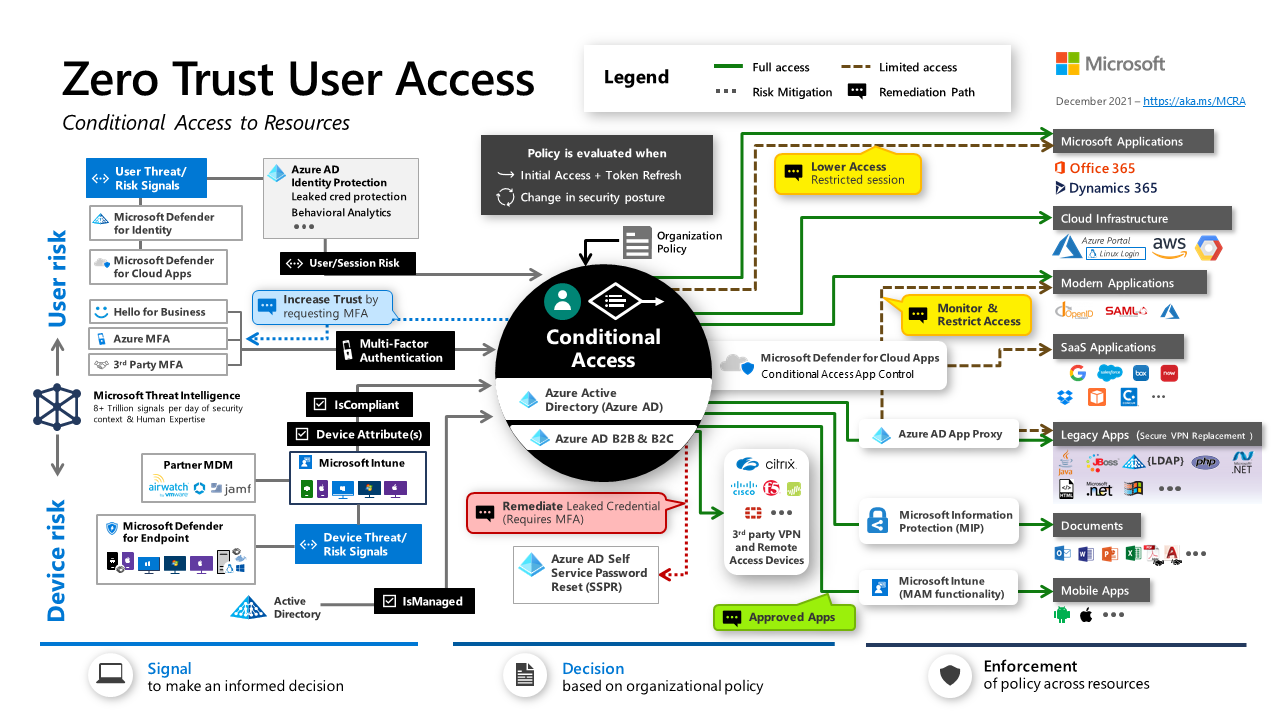
| + | https://learn.microsoft.com/en-us/azure/architecture/guide/security/images/user-access.png | ||
| + | |||
| + | |||
{|<!-- T --> | {|<!-- T --> | ||
| valign="top" | | | valign="top" | | ||
| Line 221: | Line 249: | ||
|} | |} | ||
|}<!-- B --> | |}<!-- B --> | ||
| + | {|<!-- T --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>1p5G1-4s1r0</youtube> | ||
| + | <b>Zero Trust on AWS | AWS Events | ||
| + | </b><br>Zero Trust on AWS | AWS Events | ||
| + | |} | ||
| + | |<!-- M --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>-jshgdiyo2E</youtube> | ||
| + | <b>Zero Trust Security: Deep Dive into BeyondCorp Enterprise with Google | ||
| + | </b><br>In this session, Wursta is partnering with Google to deliver a BeyondCorp Enterprise demonstration. This deep dive will show you the product in action so you can apply it to your team, with high-level use cases and expert knowledge on why zero trust is the security framework that’s here to stay. | ||
| + | |} | ||
| + | |}<!-- B --> | ||
| + | {|<!-- T --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>Te-a0WjH4xw</youtube> | ||
| + | <b>Cisco Zero Trust Overview | ||
| + | </b><br>High level insight into how Cisco provides an holisitc approach to Zero-Trust. More than a product and a platform based approach to Zero-Trust. | ||
| + | |} | ||
| + | |<!-- M --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>bXJnYbvCbgo</youtube> | ||
| + | <b>What We Learned Implementing Zero Trust Security at Microsoft | ||
| + | </b><br>Microsoft has been on a three year journey of implementing Zero Trust. This session will share the lessons that they have learned along the way. This interactive session will walk through the company's core strategy, the five main scenarios they are working on, their design, and how they have organized the teams to ensure that the focus remains were it needs to be on the journey. | ||
| + | |} | ||
| + | |}<!-- B --> | ||
| + | = Other Cybersecurity = | ||
https://www.nist.gov/sites/default/files/styles/1400_x_1400_limit/public/images/2018/02/06/intel_heatmap.png | https://www.nist.gov/sites/default/files/styles/1400_x_1400_limit/public/images/2018/02/06/intel_heatmap.png | ||
https://www.nist.gov/sites/default/files/styles/960_x_960_limit/public/images/2018/02/06/uoc_process.png | https://www.nist.gov/sites/default/files/styles/960_x_960_limit/public/images/2018/02/06/uoc_process.png | ||
| − | + | ||
* [https://www.cfr.org/report/increasing-international-cooperation-cybersecurity-and-adapting-cyber-norms Increasing International Cooperation in Cybersecurity and Adapting Cyber Norms] | * [https://www.cfr.org/report/increasing-international-cooperation-cybersecurity-and-adapting-cyber-norms Increasing International Cooperation in Cybersecurity and Adapting Cyber Norms] | ||
* [https://www.youtube.com/watch?v=GqmQg-cszw4&list=PLUl4u3cNGP62K2DjQLRxDNRi0z2IRWnNh&index=1 Cybersecurity Systems Security | MIT] | * [https://www.youtube.com/watch?v=GqmQg-cszw4&list=PLUl4u3cNGP62K2DjQLRxDNRi0z2IRWnNh&index=1 Cybersecurity Systems Security | MIT] | ||
* [https://www.cio.com/article/2600345/security0/11-steps-attackers-took-to-crack-target.html 11 Steps Attackers Took to Crack Target - stolen credentials of an HVAC vendor | CIO] | * [https://www.cio.com/article/2600345/security0/11-steps-attackers-took-to-crack-target.html 11 Steps Attackers Took to Crack Target - stolen credentials of an HVAC vendor | CIO] | ||
Latest revision as of 15:34, 28 April 2024
- Cybersecurity ... OSINT ... Frameworks ... References ... Offense ... NIST ... DHS ... Screening ... Law Enforcement ... Government ... Defense ... Lifecycle Integration ... Products ... Evaluating
- Risk, Compliance and Regulation ... Ethics ... Privacy ... Law ... AI Governance ... AI Verification and Validation
- Telecommunications ... Computer Networks ... 5G ... Satellite Communications ... Quantum Communications ... Agents ... AI Broadcast; Radio, Stream, TV
- Artificial General Intelligence (AGI) to Singularity ... Curious Reasoning ... Emergence ... Moonshots ... Explainable AI ... Automated Learning
- Libraries & Frameworks Overview ... Libraries & Frameworks ... Git - GitHub and GitLab ... Other Coding options
- Development ... Notebooks ... AI Pair Programming ... Codeless ... Hugging Face ... AIOps/MLOps ... AIaaS/MLaaS
- MITRE ATT&CK™
- 23 Top Cybersecurity Frameworks | CyberExperts.com
- Align to a Framework: Plan a Cybersecurity Roadmap's Route | CIS
- CIS Controls
- CIS Cybersecurity Roadmap
- NIST FedRAMP| NIST ... security for the cloud
- NIST Cybersecurity Framework| NIST - consists of standards, guidelines, and best practices to manage cybersecurity-related risk.
- Introduction to the Framework Roadmap | NIST
- FIPS 140-2 Security Requirements for Cryptographic Modules| NIST]
- ISO/IEC 27001
- ISO/IEC 15408-1 ISO/IEC Information Technology Task Force (ITTF)
- SABSA
- TOGAF
- Microsoft Cybersecurity Reference Architectures| Microsoft
- Zero Trust Rapid Modernization Plan| Microsoft
- Cybersecurity Reference Architecture | Microsoft
- Microsoft Cybersecurity Reference Architectures - Security | Microsoft
- United States Computer Emergency Readiness Team (US-CERT)
- OASIS Cyber Threat Intelligence (CTI) TC OpenC2
- Using the Cybersecurity Framework | DHS
- How STIX, TAXII and CybOX Can Help With Standardizing Threat Information
NOTE: Not necessarily restricted to artificial intelligence-based solutions.
Contents
Important Tools
Cybersecurity frameworks, architectures and roadmaps are important tools for organizations to improve their security posture and manage cyber risks. Here is some information about them from various sources:
Cybersecurity Frameworks
A cybersecurity framework is a set of standards, guidelines and best practices that help organizations to assess and improve their ability to prevent, detect and respond to cyber threats. A cybersecurity framework can help organizations to:
- Define their current and desired security state
- Identify and prioritize gaps and risks
- Align security activities with business goals and requirements
- Communicate and collaborate with internal and external stakeholders
- Demonstrate compliance with regulations and industry standards
Some examples of cybersecurity frameworks are:
- NIST Cybersecurity Framework (CSF): A voluntary framework developed by the National Institute of Standards and Technology (NIST) for critical infrastructure sectors in the US, but widely adopted by other sectors and countries as well. The CSF consists of five core functions: Identify, Protect, Detect, Respond and Recover. Each function has a set of categories, subcategories and informative references that provide guidance on specific security outcomes.
- NIST Cybersecurity Framework 2.0 Reference Tool | NIST ... allows users to explore the Draft CSF 2.0 Core (Functions, Categories, Subcategories, Implementation Examples) and offers human and machine-readable versions of the draft Core (in both JSON and Excel formats). Currently, the tool allows users to view and export portions of the Core using key search terms. This tool will ultimately enable users to create their own version of the CSF 2.0 Core with selected Informative References and will provide a simple and streamlined way for users to explore different aspects of the CSF Core.
- ISO/IEC 27001: An international standard for information security management systems (ISMS) that specifies the requirements for establishing, implementing, maintaining and improving an ISMS. The standard covers all aspects of information security, including risk assessment, policies, procedures, controls, monitoring, auditing and improvement. The standard also provides a certification scheme for organizations that want to demonstrate their compliance.
- CIS Controls: A set of 20 prioritized and actionable security controls developed by the Center for Internet Security (CIS) based on the most common and effective practices observed in real-world incidents. The CIS Controls cover both technical and organizational aspects of security, such as inventory, configuration, vulnerability management, access control, incident response and awareness training. The CIS Controls also provide implementation guidance for different types of organizations, such as small businesses, enterprises and cloud environments.
Cybersecurity Architectures
A cybersecurity architecture is a design or blueprint that describes how security components and processes are organized, integrated and configured to protect an organization's assets, data and operations from cyber threats. A cybersecurity architecture can help organizations to:
- Define the scope and boundaries of their security domain
- Identify and classify their assets, data and operations
- Select and implement appropriate security controls and technologies
- Define roles and responsibilities for security management and operations
- Establish security policies, standards and procedures
- Monitor and measure security performance and effectiveness
Some examples of cybersecurity architectures are:
- Microsoft Cybersecurity Reference Architectures (MCRA): A set of detailed technical diagrams that describe Microsoft's cybersecurity capabilities and how they integrate with Microsoft platforms and third-party platforms, such as Microsoft 365, Azure, ServiceNow, Salesforce, AWS and GCP. The MCRA covers various topics such as zero trust user access, security operations, operational technology (OT), multi-cloud and cross-platform capabilities, attack chain coverage, Azure native security controls and security organizational functions.
- SABSA: A framework and methodology for developing business-driven, risk-based and architecture-led security solutions. SABSA stands for Sherwood Applied Business Security Architecture. The framework consists of six layers: contextual (business), conceptual (architecture), logical (design), physical (implementation), component (build) and operational (management). Each layer has a set of attributes that define the security requirements, objectives, functions, services, components and metrics.
- TOGAF: A framework for enterprise architecture that provides a comprehensive approach to planning, designing, implementing and governing an organization's information technology. TOGAF stands for The Open Group Architecture Framework. The framework consists of four domains: business (strategy), data (information), application (system) and technology (infrastructure). Each domain has a set of principles, standards, models and views that guide the architecture development process.
Cybersecurity Roadmaps
A cybersecurity roadmap is a plan or strategy that outlines the steps and actions that an organization needs to take to achieve its security goals and objectives. A cybersecurity roadmap can help organizations to:
- Align their security initiatives with their business vision and mission
- Communicate their security vision and direction to stakeholders
- Prioritize their security investments and resources
- Track their progress and performance against their targets
- Adapt to changing threats, technologies and business needs
Some examples of cybersecurity roadmaps are:
- NIST Cybersecurity Framework Roadmap: A companion document to the NIST CSF that identifies key activities planned for improving and enhancing the CSF. The roadmap is not exhaustive in describing all planned activities within NIST but focuses on high-priority areas for development, alignment and collaboration. The roadmap version 1.1 identifies 14 areas such as confidence mechanisms, cyberattack lifecycle, cybersecurity workforce, cyber supply chain risk management, federal agency cybersecurity alignment, governance and enterprise risk management etc.
- Zero Trust Rapid Modernization Plan (RaMP): A part of the MCRA that provides a practical and actionable approach to implementing zero trust principles and practices in an organization. The RaMP consists of four phases: assess, plan, execute and optimize. Each phase has a set of steps, activities and deliverables that help organizations to define their zero trust vision, identify their current state and gaps, prioritize and implement zero trust capabilities and measure and improve their zero trust maturity.
- CIS Cybersecurity Roadmap: A guide for small and medium-sized businesses (SMBs) to improve their cybersecurity posture using the CIS Controls. The roadmap provides a simple and practical way to implement the CIS Controls based on three levels of security maturity: basic, foundational and organizational. The roadmap also provides tips, resources and tools to help SMBs with their security journey.
Making Sense
|
|
|
|
|
|
Trusted Internet Connections (TIC) 3
- Trusted Internet Connections | Cybersecurity & Infrastructure Security Agency, Department of Homeland Security (DHS)
|
|
Zero Trust
YouTube ... Quora ...Google search ...Google News ...Bing News
- Perspective ... Context ... In-Context Learning (ICL) ... Transfer Learning ... Out-of-Distribution (OOD) Generalization
- Causation vs. Correlation ... Autocorrelation ...Convolution vs. Cross-Correlation (Autocorrelation)
- Policy ... Policy vs Plan ... Constitutional AI ... Trust Region Policy Optimization (TRPO) ... Policy Gradient (PG) ... Proximal Policy Optimization (PPO)
- Architectures for AI ... Enterprise Architecture (EA) ... Enterprise Portfolio Management (EPM) ... Architecture and Interior Design
- Immersive Reality ... Metaverse ... Omniverse ... Transhumanism ... Religion
- Telecommunications ... Computer Networks ... 5G ... Satellite Communications ... Quantum Communications ... Communication Agents ... Smart Cities ... Digital Twin ... Internet of Things (IoT)
- Risk, Compliance and Regulation ... Ethics ... Privacy ... Law ... AI Governance ... AI Verification and Validation
- Cybersecurity ... OSINT ... Frameworks ... References ... Offense ... NIST ... DHS ... Screening ... Law Enforcement ... Government ... Defense ... Lifecycle Integration ... Products ... Evaluating
- Zero Trust Architecture | NIST
- Conditional Access design principles and dependencies | Microsoft
- Zero trust security model | Wikipedia
Zero Trust architecture is a cybersecurity approach that assumes breaches will occur and uses risk-based access controls to limit the damage from an attack. Instead of only guarding an organization’s perimeter, Zero Trust architecture protects each file, email, and network by authenticating every identity and device. Rather than just securing one network, Zero Trust architecture also helps secure remote access, personal devices, and third-party apps. The principles of Zero Trust are: Verify explicitly, Use least privileged access, Assume breach and Require end-to-end encryption.
Never trust, always verify
Part of... software-defined networking (SD-WAN) and Secure Access Service Edge (SASE). SASE delivers wide-area networking with cybersecurity both on-site and in the cloud as DoD expands its reliance on cloud data storage. One of the key tenants of zero trust involves identity. Thunderdome will use identity verification, including public key infrastructure (PKI), which uses a certificate to validate data being sent from one point to another, and identity credentialing and access management (ICAM). ICAM verifies a person’s identity and links them to their allowed access privileges. - Thunderdome hits its targets, DISA moves to next phase of zero trust | Alexandra Lohr - Federal New Network
- Software-defined networking (SD-WAN)
- What Is Secure Access Service Edge (SASE)? | CISCO ... a network architecture that combines VPN and SD-WAN capabilities with cloud-native security functions such as secure web gateways, cloud access security brokers, firewalls, and zero-trust network access. These functions are delivered from the cloud and provided as a service by the SASE vendor.
- Identity credentialing and access management (ICAM) ... ensure that the right person with the right privileges can access the right information at the right time
- Thunderdome is a network architecture program; laying a zero-trust technology foundation
- US Defense Information Systems Agency (DISA)
|
|
|
|
|
|
|
|
Other Cybersecurity

