Lie Detection
YouTube search... ...Google search
- Risk, Compliance and Regulation ... Ethics ... Privacy ... Law ... AI Governance ... AI Verification and Validation
- Cybersecurity ... OSINT ... Frameworks ... References ... Offense ... NIST ... DHS ... Screening ... Law Enforcement ... Government ... Defense ... Lifecycle Integration ... Products ... Evaluating
- A New AI That Detects “Deception” May Bring an End to Lying as We Know It
- AI Lie Detectors Could Soon Police the Borders
- Automated Virtual Agent for Truth Assessments in Real-Time (AVATAR) | CNBC - Lie-detecting computer kiosks equipped with artificial intelligence look like the future of border security
- EyeDetect | Converus
- A Survey of Automatic Facial Micro-expression Analysis: Databases, Methods and Challenges | Y. Oh, J. See, A.C. Le Ngo, R.C.W. Phan, and V.M.Baskaran
- AI Lie Detectors Could Soon Police the Borders | Kevin McCaney - governmentCIO
Predictions of high-level micro-expressions can be used as features for deception prediction. Surprisingly, IDT (Improved Dense Trajectory) features which have been widely used for action recognition, are also very good at predicting deception. DARE: Deception Analysis and Reasoning Engine | Z. Wu, B. Singh, L.S. Davis, and V. S. Subrahmanian AI technology has made significant advancements in various fields, including lie detection. By leveraging Machine Learning (ML) algorithms and Natural Language Processing (NLP) techniques, AI systems are being developed to analyze verbal and non-verbal cues, helping to identify deception patterns and improve the accuracy of lie detection. These AI-based lie detection systems have the potential to be used in various domains, such as law enforcement, security, and criminal investigations. However, it's important to note that AI lie detection is still an evolving field, and there are ethical considerations and limitations to be taken into account. Ongoing research and advancements in this field will shape the future of AI-based lie detection and its potential impact on various domains.
- Research and Techniques: Researchers have explored different approaches to incorporate AI into lie detection processes. One commonly used technique is Sentiment Analysis, where AI algorithms analyze the emotional content of verbal or written statements. By analyzing the words, tone, and expressions used, these systems can infer the underlying emotions and potential deception. Another approach is based on facial recognition and analysis. AI algorithms can examine facial microexpressions, which are brief facial expressions that occur involuntarily and are difficult to control. These microexpressions, which may last for just a fraction of a second, can reveal hidden emotions and potentially indicate deception. Natural Language Processing (NLP) plays a crucial role in AI lie detection systems. NLP algorithms are trained on large datasets of text, enabling them to understand and interpret the meaning of words and phrases in context. This allows AI systems to identify linguistic patterns and anomalies that may be indicative of deception.
- Limitations and Ethical Considerations: While AI holds promise in lie detection, there are several limitations and ethical considerations that must be addressed. AI systems are trained on existing data, which can introduce biases and inaccuracies. If the training data is biased or incomplete, it can lead to unfair outcomes and false accusations. Moreover, the interpretation of non-verbal cues and microexpressions can be subjective. Different individuals may exhibit varying facial expressions and body language, making it challenging to establish universal standards for deception detection. Additionally, cultural and individual differences can influence the interpretation of these cues, further complicating the accuracy of AI lie detection systems.
- Legal and Privacy Implications: The use of AI in lie detection raises legal and privacy concerns. In many jurisdictions, the admissibility of evidence obtained through AI lie detection systems is still a subject of debate. Ensuring that these systems comply with legal standards and do not violate individuals' rights to privacy and due process is crucial. Furthermore, AI-based lie detection systems often require substantial amounts of personal data to function effectively. Safeguarding this data and ensuring its proper handling is essential to protect individuals' privacy. Striking a balance between the potential benefits of AI lie detection and safeguarding individual rights is a critical consideration for policymakers and researchers in this field.

iBorderCtrl
“lie detection” is just a portion of what iBorderCtrl does.
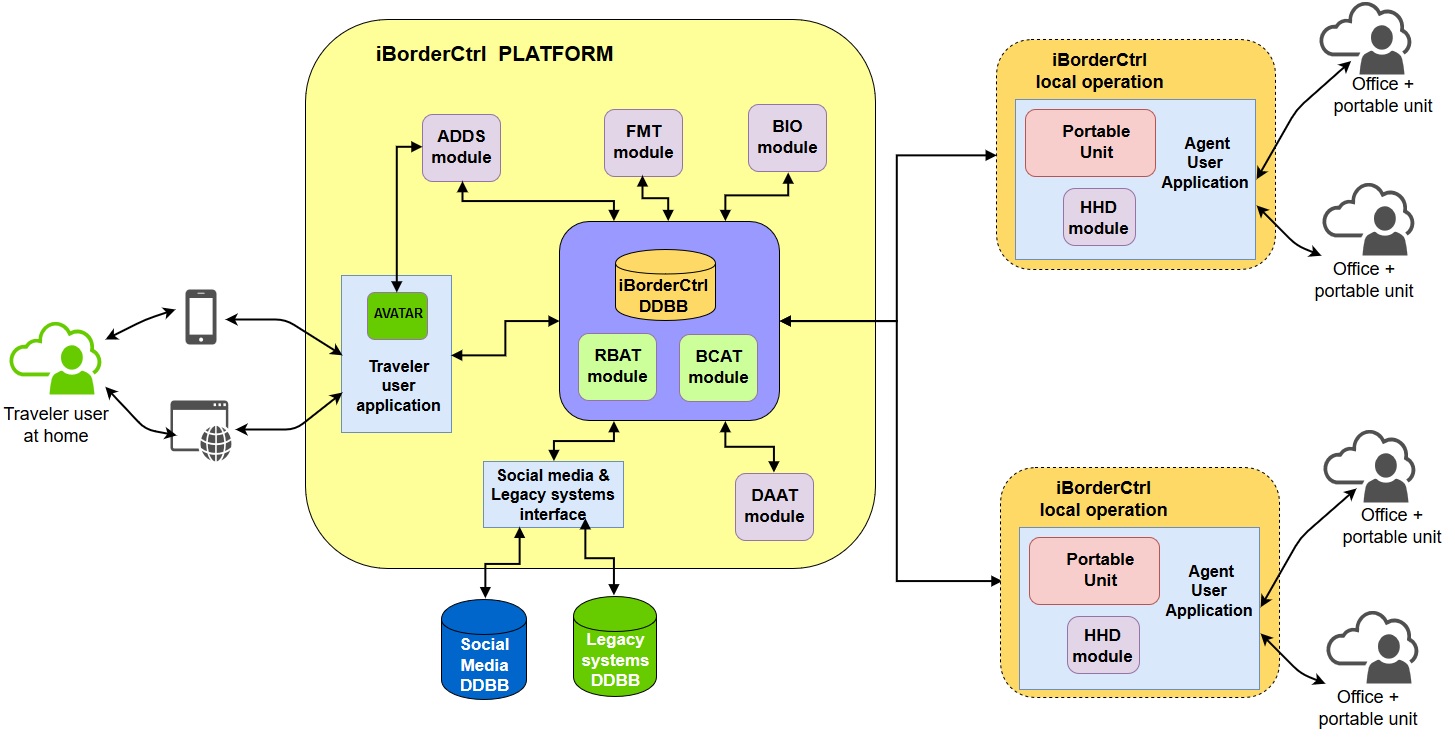
The main modules that consist the overall solution are the following:
- The Automatic Deception Detection System (ADDS)* performs, controls and assesses the pre-registration interview by sequencing a series of questions posed to travellers by an Avatar. ADDS quantifies the probability of deceit in interviews by analysing interviewees non-verbal micro expressions. This, coupled with an avatar, moves this novel approach to deception detection to the pre-registration phase resulting in its deployment without an impact to the time spend at the border crossing by the traveller. The avatar also allows for a consistent and controllable stimuli across interviews in terms of both the verbal and non-verbal from the direction of the avatar agent to the traveller personalized to gender and language of the traveller, reducing variability compared to human interviewers and potentially improving the accuracy of the system. Despite the large use of biometrics on security applications including in border control with the advent of digital passports that contain fingerprints digital images and physical characteristics of individuals, a traveller with ill intentions using own documents, biomarkers would not reveal their attempted deceit. iBorderCtrl deploys well established as well as novel technologies together to collect data that will move beyond biometrics and onto biomarkers of deceit.
- The Biometrics Module incorporating fingerprints and palm vein technologies (BIO module), for the biometric identity validation of the traveller. The BIO module is used at the Border Crossing and two different scanners are used respectively. In both cases the fingerprints and/or palm vein images are compared to the relevant information stored in databases (legacy systems in the case of fingerprints and creation of a baseline database for palm vein images) in order to assist the Border Guards to validate the traveller’s identity.
- the Face Matching Tool (FMT), receives images of the traveller (both video type and photo) in order to create at first their biometric signature. This biometric model is compared with future images of similar type obtained from the traveller during both pre-registration phase and border crossing, in order to provide a matching score.
- The Document Authenticity Analytics Tool (DAAT) is used both at the pre-registration and the border control procedures. DAAT is responsible for the verification procedure of travel documents which the traveller provided himself during the pre-registration procedure and the border guards scanned during the border control check. The security features of travel documents (passport, visa) are examined by DAAT against fraud characteristics in an automated way. Thus, a matching score concerning the validation of the documents authenticity is derived to facilitate the Border Guards to identify fraud characteristics.
- The Hidden Human Detection Tool (HHD) supports the Border Guard in searching and detecting hidden people inside various vehicles (i.e. passengers attempting illegal border crossing). This tool is foreseen for the Border Crossing procedure to assist the Border Guard in the field. The functionality provided is the detection of humans hidden within vehicles such as cars or closed compartments (containers carried on trucks or train wagons).
- The External Legacy and Social interfaces system (ELSI), is used to crosscheck the traveller’s information from legacy systems, such as SIS II, providing the necessary interoperability interfaces.
- The Risk Based Assessment Tool (RBAT), implements a risk–assessment routine which aggregates and correlates the risks estimations received by the processing of the travellers’ data and documents supporting the decision-making of the border guard. RBAT enables a common, harmonised model for risk management and implements a systematic process to stimulate compliance and prevent and/or treat the risk of non-compliance, including risk of fraud and any other risk which appears to threaten the Authorities objectives. RBAT will also identify cases that deserve further investigation, facilitating in this way better resources allocation for the Border Managers and Agents. These risks are key to the performance of the system as they declutter the information provided to the agent by compressing all data into meaningful actionable risk scores that help the agent at the border target any follow up checks and questioning to the traveller.
- The Integrated Border Control Analytics Tool (BCAT) enables advanced post-hoc analytics that will help identify new patterns and knowledge allowing the iBorderCtrl system to adapt quickly to new situations. At the same time, BCAT will evaluate the performance of each iBorderCtrl system and its effectiveness. BCAT will also discover key patterns in the data associated with either false accept or false rejects of travellers, which can be used for better decision making at border control. BCAT will also provide analysis on traffic data, so that it can provide the traffic history and the expected traffic for certain dates.
