Difference between revisions of "Cybersecurity"
m |
m |
||
| Line 2: | Line 2: | ||
|title=PRIMO.ai | |title=PRIMO.ai | ||
|titlemode=append | |titlemode=append | ||
| − | |keywords=artificial, intelligence, machine, learning, models, algorithms, data, singularity, moonshot, | + | |keywords=artificial, intelligence, machine, learning, models, algorithms, data, singularity, moonshot, TensorFlow, Google, Nvidia, Microsoft, Azure, Amazon, AWS, Facebook |
|description=Helpful resources for your journey with artificial intelligence; videos, articles, techniques, courses, profiles, and tools | |description=Helpful resources for your journey with artificial intelligence; videos, articles, techniques, courses, profiles, and tools | ||
}} | }} | ||
| Line 46: | Line 46: | ||
* [http://pathmind.com/wiki/fraud-detection Fraud and Anomaly Detection | Chris Nicholson - A.I. Wiki pathmind] | * [http://pathmind.com/wiki/fraud-detection Fraud and Anomaly Detection | Chris Nicholson - A.I. Wiki pathmind] | ||
* [http://us-cert.cisa.gov/sites/default/files/FactSheets/NCCIC%20ICS_FactSheet_CSET_S508C.pdf The Cyber Security Evaluation Tool (CSET®) | National Cybersecurity and Communications Integration Center] ...provides a systematic, disciplined, and repeatable approach for evaluating an organization’s security posture | * [http://us-cert.cisa.gov/sites/default/files/FactSheets/NCCIC%20ICS_FactSheet_CSET_S508C.pdf The Cyber Security Evaluation Tool (CSET®) | National Cybersecurity and Communications Integration Center] ...provides a systematic, disciplined, and repeatable approach for evaluating an organization’s security posture | ||
| − | * [http://www.cyberscoop.com/trickbot-takedown-cyber-command-microsoft/ Cyber Command, Microsoft take action against Trickbot botnet before Election Day | Shannon Vavra - cyberscoop] | + | * [http://www.cyberscoop.com/trickbot-takedown-cyber-command-microsoft/ Cyber Command, [[Microsoft]] take action against Trickbot botnet before Election Day | Shannon Vavra - cyberscoop] |
** [http://blogs.microsoft.com/on-the-issues/2020/10/20/trickbot-ransomware-disruption-update/ An update on disruption of Trickbot Tom Burt |] [[Microsoft]] ...The seven remaining servers are not traditional command-and-control servers but rather [[Internet of Things (IoT)]] devices | ** [http://blogs.microsoft.com/on-the-issues/2020/10/20/trickbot-ransomware-disruption-update/ An update on disruption of Trickbot Tom Burt |] [[Microsoft]] ...The seven remaining servers are not traditional command-and-control servers but rather [[Internet of Things (IoT)]] devices | ||
| − | ** [http://www.zdnet.com/article/fbi-warning-trickbot-and-ransomware-attackers-plan-big-hit-on-us-hospitals/ FBI warning: Trickbot and ransomware attackers plan big hit on US hospitals | Liam Tung - ZDNet] ...The FBI, [[Cybersecurity: National Institute of Standards and Technology (NIST) & U.S. Department of Homeland Security (DHS)|CISA]], HHS warning comes two weeks after Microsoft's partial takedown of the Trickbot botnet. | + | ** [http://www.zdnet.com/article/fbi-warning-trickbot-and-ransomware-attackers-plan-big-hit-on-us-hospitals/ FBI warning: Trickbot and ransomware attackers plan big hit on US hospitals | Liam Tung - ZDNet] ...The FBI, [[Cybersecurity: National Institute of Standards and Technology (NIST) & U.S. Department of Homeland Security (DHS)|CISA]], HHS warning comes two weeks after [[Microsoft]]'s partial takedown of the Trickbot botnet. |
* [[Watch me Build a Cybersecurity Startup]] | [[Creatives#Siraj Raval|Siraj Raval]] | * [[Watch me Build a Cybersecurity Startup]] | [[Creatives#Siraj Raval|Siraj Raval]] | ||
Revision as of 05:24, 30 October 2020
Youtube search... ...Google search
- Case Studies
- Capabilities
- Cybersecurity References
- Offense - Adversarial Threats/Attacks
- Cybersecurity Frameworks, Architectures & Roadmaps
- Cybersecurity Companies/Products
- Cybersecurity: Evaluating & Selling
- (Artificial) Immune System
- 5G Security
- AIOps / MLOps
- Cybersecurity - Gaming
- Useful Models ...find outliers:
- Time
- Government’s AI Odyssey - A Candid Poll on AI and Machine Learning in the Federal Government | Government Business Council - AWS
- Bayesian Poisoning is a technique used by e-mail spammers to attempt to degrade the effectiveness of spam filters that rely on Bayesian spam filtering
- Detecting Malicious Requests with Keras & TensorFlow | Adam Kusey - Medium
- Best security software: How 12 cutting-edge tools tackle today's threats | CSO
- Graph
- Intelligence Advanced Research Projects Activity (IARPA)Is Trying Keep Adversaries From Corrupting AI Tools ... Could cyber adversaries be training the government’s artificial intelligence tools to fail? | Jack Corrigan - Nextgov
- TrojAI - Office of the Director of National Intelligence Office: Intelligence Advanced Research Projects Activity FedBizOpps.gov predict whether AI systems have been corrupted through so-called “Trojan attacks.”
- Adversarial Attacks on Graph Convolutional Network (GCN), Graph Neural Networks (Graph Nets), Geometric Deep Learning
- Breaking Down the Tencent 2018 Cybersecurity Report
- Chronicle combines all the best parts of Google and X culture
- Fraud and Anomaly Detection | Chris Nicholson - A.I. Wiki pathmind
- The Cyber Security Evaluation Tool (CSET®) | National Cybersecurity and Communications Integration Center ...provides a systematic, disciplined, and repeatable approach for evaluating an organization’s security posture
- Cyber Command, Microsoft take action against Trickbot botnet before Election Day | Shannon Vavra - cyberscoop
- An update on disruption of Trickbot Tom Burt | Microsoft ...The seven remaining servers are not traditional command-and-control servers but rather Internet of Things (IoT) devices
- FBI warning: Trickbot and ransomware attackers plan big hit on US hospitals | Liam Tung - ZDNet ...The FBI, CISA, HHS warning comes two weeks after Microsoft's partial takedown of the Trickbot botnet.
- Watch me Build a Cybersecurity Startup | Siraj Raval
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Fraud Detection
- Introduction to Fraud Detection Systems | Miguel Gonzalez-Fierro, Microsoft
- AI for Health Insurance Fraud Detection – Current Applications | Niccolo Mejia
|
|
|
|
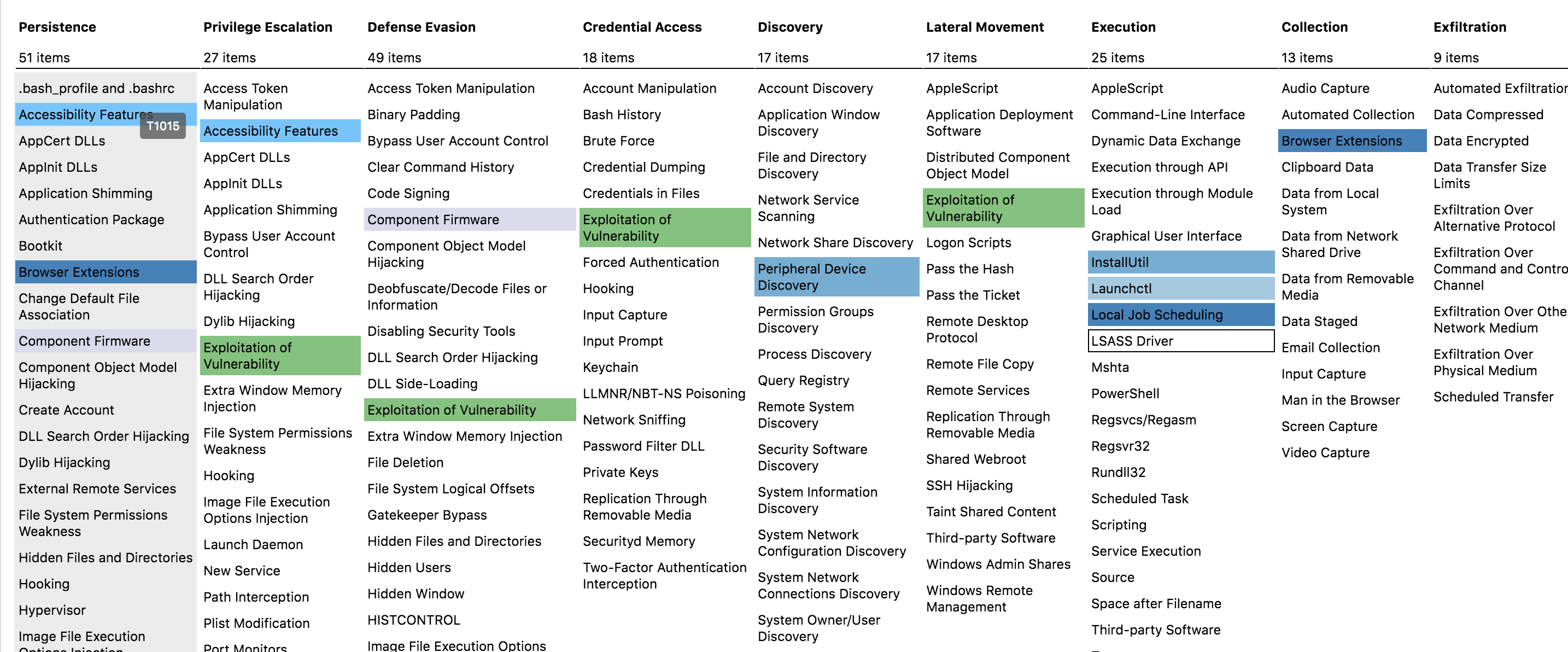
MITRE ATT&CK™
Youtube search... ...Google search
- ATT&CK™ Navigator | MITRE ...measure your threat detection
- ATT&CK™ Homepage | MITRE
- ATT&CK™ Resources | MITRE
- MITRE ATT&CK™ Framework: Everything You Need to Know | Jeff Petters - Varonis
- DETT&CT: MAPPING YOUR BLUE TEAM TO MITRE ATT&CK™ | Marcus Bakker and Ruben Bouman - MB Secure ...DEtect Tactics, Techniques & Combat Threats
- Remapping Red Canary with ATT&CK sub-techniques | B. Donohue, K. Nickels, and M. Graeber - Atomic Red Team; a library of simple tests that every security team can execute to test their defenses.
- Using the OODA Loop - Purple Team with Cybersecurity
knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK™ knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.

|
|
|
|
|
|
Data Center Security
Youtube search... ...Google search
|
|
|
|
|
|