Difference between revisions of "Telecommunications"
m (→5G) |
m |
||
| Line 188: | Line 188: | ||
* [[Telecommunications]] ... [[Computer Networks]] ... [[Telecommunications#5G|5G]] ... [[Satellite#Satellite Communications|Satellite Communications]] ... [[Quantum Communications]] ... [[Agents#Communication | Communication Agents]] ... [[Smart Cities]] ... [[Digital Twin]] ... [[Internet of Things (IoT)]] | * [[Telecommunications]] ... [[Computer Networks]] ... [[Telecommunications#5G|5G]] ... [[Satellite#Satellite Communications|Satellite Communications]] ... [[Quantum Communications]] ... [[Agents#Communication | Communication Agents]] ... [[Smart Cities]] ... [[Digital Twin]] ... [[Internet of Things (IoT)]] | ||
| − | * [[Immersive Reality]] ... [[Metaverse]] ... [[ | + | * [[Immersive Reality]] ... [[Metaverse]] ... [[Omniverse]] ... [[Transhumanism]] ... [[Religion]] |
* [https://www.3gpp.org/dynareport/SpecList.htm?release=Rel-15&tech=4 3rd Generation Partnership Project (3GPP)] ...unites [Seven] telecommunications standard [[development]] organizations: ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC | * [https://www.3gpp.org/dynareport/SpecList.htm?release=Rel-15&tech=4 3rd Generation Partnership Project (3GPP)] ...unites [Seven] telecommunications standard [[development]] organizations: ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC | ||
* [https://www.ietf.org/blog/5g-and-internet-technology/ Internet Engineering Taskforce (IETF)] | * [https://www.ietf.org/blog/5g-and-internet-technology/ Internet Engineering Taskforce (IETF)] | ||
Revision as of 20:00, 19 March 2024
Youtube search... ...Google search
- Telecommunications ... Computer Networks ... 5G ... Satellite Communications ... Quantum Communications ... Communication Agents ... Smart Cities ... Digital Twin ... Internet of Things (IoT)
- Cybersecurity ... OSINT ... Frameworks ... References ... Offense ... NIST ... DHS ... Screening ... Law Enforcement ... Government ... Defense ... Lifecycle Integration ... Products ... Evaluating
- Zero Trust
- Time ... PNT ... GPS ... Retrocausality ... Delayed Choice Quantum Eraser ... Quantum
- Ericsson launches unique AI functionality to boost radio access networks
- Deepsig pioneering the application of deep learning to wireless
- How Machine Learning Is Creating New Opportunities In The Telecommunications Industry | Julie Stoughton - Digitalist Magazine
- Top 10 Data Science Use cases in Telecom | Igor Bobriakov - Medium
AI has been applied in the telecommunications industry for over a decade, with applications focused on optimizing radio signals, power management, and network performance. AI algorithms can analyze data from network sensors to identify potential problems before they occur, allowing telecom providers to take proactive steps to fix problems and prevent outages. AI can also help to optimize network performance, improve customer service, equipment maintenance, and fraud detection. Implementing AI in telecoms also allows CSPs to proactively fix problems with communications hardware, such as cell towers. AI has the potential to simplify the task of operations by optimizing various functions that make up operations, such as field and service operations. Telecom operators can develop new revenue sources for themselves by examining market niches they haven’t previously. Some of the most promising applications of artificial intelligence and data science in telecommunications include fraud detection, customer experience improvement, and optimizing mobile tower operations.
Contents
Cognitive Radio (CR) / Software-defined radio (SDR)
Software-defined radio (SDR) is a radio communication system where components that have been traditionally implemented in hardware (e.g. mixers, filters, amplifiers, modulators/demodulators, detectors, etc.) are instead implemented by means of software on a personal computer or embedded system. Software radios have significant utility for the military and cell phone services, both of which must serve a wide variety of changing radio protocols in real time. In the long term, software-defined radios are to become the dominant technology in radio communications. SDRs, along with software defined antennas are the enablers of the cognitive radio.
GNU Radio
is a free & open-source software development toolkit that provides signal processing blocks to implement software radios. It can be used with readily-available low-cost external RF hardware to create software-defined radios, or without hardware in a simulation-like environment.
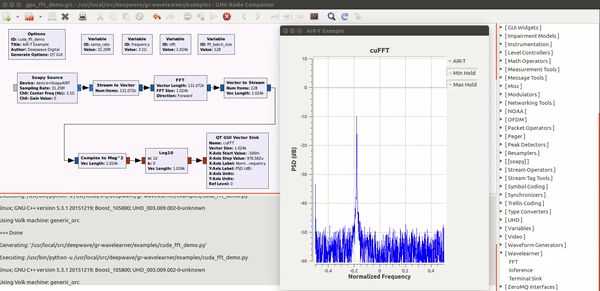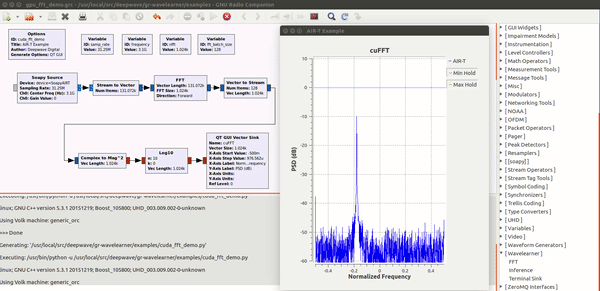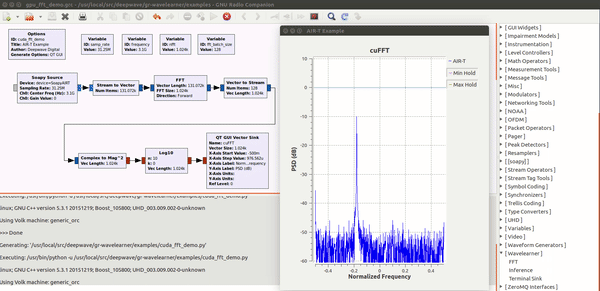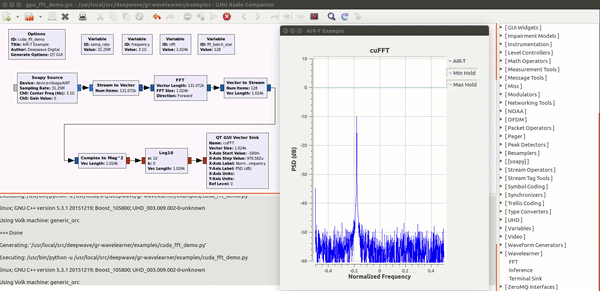
Deepwave Digital Systems
Enabling deep learning and AI at the edge of wireless systems. GPUs are extremely well suited for processes that are highly parallel. The Fast Fourier Transform (FFT) is one of the most common techniques in signal processing and happens to be a highly parallel algorithm. In this blog post the Deepwave team walks you though how to leverage the embedded GPU built into the AIR-T to perform high-speed FFTs without the computational bottleneck of a CPU and without having to experience the long development cycle associated with writing VHDL code for FPGAs. By leveraging the GPU on the AIR-T, you get the best of both worlds: fast development time and high speed processing. A familiar tool to anyone working in the wireless domain, GNU Radio allows signal processing experts to tie together blocks of functionality using an intuitive GUI. Many of the “in the weeds” details regarding the software implementation are well abstracted so the user can focus on the algorithm instead.Once an algorithm has been optimized (or a pre-trained algorithm has been downloaded by a 3rd party), the user will reference it in Deepwave’s GR-WAVELEARNER software that provides a TensorRT Inference block for GNU Radio Companion (GRC)

Software-Defined Networking (SDN)
YouTube ... Quora ... Google search ... Google News ... Bing News
Artificial Intelligence (AI) can assist Software-Defined Networking (SDN) in several ways. One of the main benefits of AI in SDN is the ability to automate network management tasks, which can help to reduce the workload on network administrators and improve network performance. AI can be used to analyze network traffic patterns and predict network failures or congestion, allowing network administrators to take proactive measures to prevent these issues from occurring. AI can also be used to optimize network traffic routing and load balancing, which can improve network performance and reduce latency.
Another way that AI can assist SDN is by enabling more intelligent network security. AI can be used to detect and respond to security threats in real-time, allowing network administrators to quickly identify and mitigate potential security breaches. AI can also be used to analyze network traffic patterns and identify anomalies that may indicate a security threat.
AI can also assist SDN in network optimization. AI algorithms can be used to optimize network traffic routing and load balancing, which can improve network performance and reduce latency. AI can also be used to optimize network resource allocation, ensuring that network resources are allocated efficiently and effectively.
SDN & SD-WAN
Software-Defined Networking (SDN) is an approach to network management that enables dynamic, programmatically efficient network configuration in order to improve network performance and monitoring. SDN is meant to address the fact that the static architecture of traditional networks is decentralized and complex while current networks require more flexibility and easy troubleshooting. SDN suggests to centralize network intelligence in one network component by disassociating the forwarding process of network packets (data plane) from the routing process (control plane). The control plane consists of one or more controllers which are considered as the brain of SDN network. The data plane is composed of OpenFlow-enabled switches which are responsible for the packet forwarding between hosts. The communication between the control and data planes is through the OpenFlow protocol.
SD-WAN (Software-Defined Wide Area Network) is an extension of SDN that applies SDN principles to WAN connections. SD-WAN simplifies the management and operation of a WAN by decoupling the networking hardware from its control mechanism. This concept is similar to how software-defined networking implements virtualization technology to improve data center management and operation. A key application of SD-WAN is to allow companies to build higher-performance WANs using lower-cost and commercially available Internet access, enabling businesses to partially or wholly replace more expensive private WAN connection technologies such as MPLS
Machine learning solving practical problems in Communications
Machine learning has been applied to solve various practical problems in communications. Here are some examples:
- Channel Estimation: Channel estimation is a crucial task in wireless communications, where the goal is to estimate the channel response between the transmitter and the receiver. Machine learning techniques have been used to improve the accuracy of channel estimation, especially in scenarios where the channel is time-varying and the traditional methods fail to provide accurate estimates.
- Modulation Classification: Modulation classification is the task of identifying the modulation scheme used in a wireless transmission. Machine learning algorithms have been used to classify the modulation schemes based on the received signal, which can be useful in cognitive radio systems, where the radio can adapt its transmission parameters based on the modulation scheme used by the primary user.
- Signal Detection: Signal detection is the task of detecting the presence of a signal in a noisy environment. Machine learning algorithms have been used to improve the detection performance, especially in scenarios where the signal-to-noise ratio is low and the traditional methods fail to provide reliable detection.
- Resource Allocation: Resource allocation is the task of allocating the available resources, such as power and bandwidth, among the users in a wireless network. Machine learning algorithms have been used to optimize the resource allocation based on the network conditions and the user requirements, which can improve the network performance and the user experience.
- Interference Mitigation: Interference mitigation is the task of reducing the interference caused by other users in a wireless network. Machine learning algorithms have been used to mitigate the interference by predicting the interference patterns and adapting the transmission parameters accordingly.
Physical Layer Security (PLS)
Youtube search... ...Google search
Physical layer security (PLS) has emerged as a new concept and powerful alternative that can complement and may even replace encryption-based approaches, which entail many hurdles and practical problems for future wireless systems. The basic idea of PLS is to exploit the characteristics of the wireless channel and its impairments including noise, fading, interference, dispersion, diversity, etc. in order to ensure the ability of the intended user to successfully perform data decoding while preventing eavesdroppers from doing so. Thus, the main design goal of PLS is to increase the performance difference between the link of the legitimate receiver and that of the eavesdropper by using well-designed transmission schemes. Physical Layer Security for Downlink NOMA: Requirements, Merits, Challenges, and Recommendations | H. Furqan, J. Hamamreh, and H. Arslan
Waveform
Youtube search... ...Google search
- Signal Processing
- Secure waveform development and test | Rohde & Schwarz
- What is it with Waveforms? | Thomas Withington - Armada International
- Secure Waveforms | Riverside Research ... Defending Our Future with Secure Waveforms
- Wraith™ Waveform Provides Truly Resilient Communications For The Tactical Edge | L3Harris
- Advanced Low Probability of Intercept/Low Probability of Detection Radar (LPI/LPD) Techniques Using Artificial Intelligence Driven Methods | SBIR.gov
- Clear Communications in the Shadows | Andrew White - Armada International
- Clutter-Masked Waveform Design for LPI/LPD Radarcom Signal Encoding | R. Washington, B. Bischof, D. Garmatyuk, & S. Mudaliar ... obtained clutter models are used for random sequence encoding of radar-communication (radarcom) signals to achieve clutter-masked transmissions and improve communication security.
Secure waveforms are designed to minimize the probability of detection by adversaries, making it difficult for them to intercept or jam the communication. AI can support secure waveforms by developing advanced techniques that can optimize the waveform parameters and minimize the probability of detection by adversaries. Artificial Intelligence (AI) can support secure waveforms in several ways:
- Signal Processing: AI can be used to develop advanced signal processing techniques that can detect and extract weak signals from noisy environments. These techniques can help LPI/LPD waveforms to remain undetected by adversaries by minimizing the signal's footprint and reducing the probability of detection.
- Cognitive Radio: AI can be used to develop cognitive radio systems that can adapt to the changing radio environment and optimize the waveform parameters to minimize the probability of detection. These systems can use machine learning algorithms to learn from the radio environment and adjust the waveform parameters, such as frequency, modulation, and power, to maintain LPI/LPD characteristics.
- Machine Learning (ML): AI can be used to develop machine learning algorithms that can analyze the radio environment and predict the probability of detection. These algorithms can use various features, such as signal strength, frequency, and modulation, to predict the probability of detection and optimize the waveform parameters to maintain LPI/LPD characteristics.
- Cybersecurity: AI can be used to develop advanced cybersecurity techniques that can detect and prevent jamming and interception attempts by adversaries. These techniques can use machine learning algorithms to analyze the radio environment and detect anomalous activities that indicate jamming or interception attempts.
Secure Waveforms
Secure waveforms refer to communication waveforms that are designed to provide secure and resilient communication in various wireless communication systems. These waveforms are specifically designed to mitigate vulnerabilities and protect against various types of attacks, ensuring the confidentiality, integrity, and availability of transmitted data. Secure waveforms typically incorporate advanced encryption techniques, authentication mechanisms, and error correction codes to enhance the security and reliability of wireless communication. They are often used in military, defense, and critical infrastructure applications where secure and resilient communication is of utmost importance. Attributes are:
- Confidentiality: Confidentiality ensures that the information transmitted using the waveform remains private and cannot be accessed or understood by unauthorized entities. This is achieved through encryption techniques, where the waveform data is encrypted using cryptographic algorithms. Only authorized recipients with the appropriate decryption keys can decrypt and access the original information.
- Integrity: Integrity ensures that the waveform data remains unchanged during transmission and cannot be tampered with by unauthorized entities. To achieve integrity, secure waveforms use techniques such as message authentication codes (MACs) or digital signatures. These techniques allow the recipient to verify the integrity of the received waveform by checking the authenticity of the transmitted data.
- Authentication: Authentication ensures that the communicating entities can verify each other's identities to establish trust and prevent unauthorized access. Secure waveforms use authentication mechanisms such as digital certificates, public-key infrastructure (PKI), or challenge-response protocols. These mechanisms allow entities to verify the identity of the sender and ensure that the received waveform is from a trusted source.
- Anti-jamming: Anti-jamming capabilities protect the waveform from intentional interference or jamming attempts by adversaries. Secure waveforms employ techniques such as frequency hopping, spread spectrum modulation, or adaptive modulation to mitigate the effects of jamming. These techniques make it difficult for adversaries to disrupt or interfere with the transmission, ensuring reliable and secure communication. Some of the techniques used in secure waveforms to provide anti-jamming capabilities are:
- Frequency hopping: In frequency hopping, the transmitter and receiver switch between different frequencies in a pre-determined pattern. This makes it difficult for an adversary to jam the signal as they would need to jam all the frequencies being used.
- Spread spectrum: In spread spectrum, the signal is spread over a wide frequency band using a code. The receiver uses the same code to de-spread the signal. This makes it difficult for an adversary to jam the signal as they would need to jam the entire frequency band.
- Adaptive power control: In adaptive power control, the transmitter adjusts its power based on the received signal strength. This helps to maintain a constant signal-to-noise ratio and makes it difficult for an adversary to jam the signal by overpowering it.
- Directional antennas: In directional antennas, the transmitter and receiver use antennas that focus the signal in a specific direction. This makes it difficult for an adversary to jam the signal as they would need to be in the path of the signal.
Anti-Jam (AJ) & Low Probability of Intercept/Detection (LPI/ LPD) Waveforms
With MIMO arrays, radios like the StreamCaster are able to eliminate interference by directing a null toward a jammer. This happens via an optional software module called MANET-Interference Cancellation (MAN-IC). MAN-IC listens to the spatial signature of a jamming signal, then computes a set of antenna weights that null out that spatial signature. This method has proven extremely powerful, yielding as much as 30 dB of consistent suppression in field trials. The module also has the secondary benefit of improving LPI/LPD performance. By utilizing a friendly cover signal, radios can operate on the same frequencies by nulling the friendly “jamming” signal. The friendly signal overpowers the much weaker communications signals of those radios, hiding these weaker signals from the enemy.
Primary, Alternative, Contingency and Emergency (PACE) communications
Another module called MANET-Interference Avoidance (MAN-IA) enables military radios to avoid interference by hopping to a different frequency band. The system monitors multiple frequencies in different bands using the MIMO degrees of freedom available in the radios. Once the radios detect a jamming signal, each radio autonomously selects the next best channel. A regrouping algorithm ensures that all radios converge on a common frequency in less than one second.
Low Probability of Intercept/Detection (LPI/ LPD)
In a MANET, radios typically operate at maximum power to ensure high throughput and high network efficiency. But this produces suboptimal LPI/LPD performance since higher power is more easily detectable by adversaries. This has led to the development of a module called MANET-Power Control (MAN-PC) that minimizes the radio’s transmit power while maintaining the desired throughput. Field tests have shown a 70 percent reduction in distance to the detector before the signal is detected.
5G
YouTube search... ...Google search
- Telecommunications ... Computer Networks ... 5G ... Satellite Communications ... Quantum Communications ... Communication Agents ... Smart Cities ... Digital Twin ... Internet of Things (IoT)
- Immersive Reality ... Metaverse ... Omniverse ... Transhumanism ... Religion
- 3rd Generation Partnership Project (3GPP) ...unites [Seven] telecommunications standard development organizations: ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC
- Internet Engineering Taskforce (IETF)
- What is 5G? | NIST
- European Telecommunications Standards Institute (ETSI) ISG Network Functions Virtualisation (NFV) - ETSI Industry Specification Group
- China Global Television Network (CGTN) | Wikipedia
- 5G + Cloud + AI: Huawei Works with Carriers to Power New ICT Infrastructure | Huawei - PR Newswire
- Armed Forces Communications and Electronics Association ...communications, information technology, intelligence and security
- MIMO | Wikipedia
|
|
|
|
|
|
5G Security
YouTube search... ...Google search
Three-step approach to reach a high level of intelligent security management. How to master E2E network security when introducing 5G core | Kari-Pekka Perttula - Ericsson
- Dynamic: Introduce automated security policy configuration and compliance monitoring
- Cognitive: Automated threat and vulnerability detection assisted with ML /AI
- Intelligent: Repeatable, adaptive and holistic security management with threat intelligence. This provides end-to-end visibility for business-related security risks, and actions can be directed via automated workflows to mitigate risks faster.
Threat Model: STRIDE | Wikipedia The threats are:
- Spoofing
- Tampering
- Repudiation
- Information disclosure (breach or data leak)
- Denial of service
- Elevation of privilege]
|
|
|
|
|
|
5G Testing
YouTube search... ...Google search
- Model_Monitoring
- DOD Kicks Off World’s Largest Dual-Use 5G Testing Effort | C. Todd Lopez - DOD News ...AT&T, Booz Allen Hamilton, Deloitte Consulting LLP, Ericsson, Federated Wireless, GBL System Corp., General Dynamics Mission Systems, Inc., GE Research, Key Bridge Wireless LLC, KPMG LLP, Nokia, Oceus Networks, Scientific Research Corporation, Shared Spectrum Company and Vectrus Mission Solutions Corporation.
|
|
Virtualization - Dynamic Spectrum Sharing (DSS)
Youtube search... ...Google search ...Google News
- Telecommunications
- Computer Networks
- Defense
- How to Know if You’re Ready to Deploy a Dark Fiber Network | Rob Coenen - Lightwave ...unused or under-utilized fiber infrastructure (including fibers, cabling, and repeaters) that was laid as part of a hedge against exponential growth in data use.
Spectrum Sharing utilizes virtualization to partition optical spectrum
|
|
|
|