Difference between revisions of "Cybersecurity"
m |
m |
||
| Line 43: | Line 43: | ||
* [http://pathmind.com/wiki/fraud-detection Fraud and Anomaly Detection | Chris Nicholson - A.I. Wiki pathmind] | * [http://pathmind.com/wiki/fraud-detection Fraud and Anomaly Detection | Chris Nicholson - A.I. Wiki pathmind] | ||
* [http://us-cert.cisa.gov/sites/default/files/FactSheets/NCCIC%20ICS_FactSheet_CSET_S508C.pdf The Cyber Security Evaluation Tool (CSET®) | National Cybersecurity and Communications Integration Center] ...provides a systematic, disciplined, and repeatable approach for evaluating an organization’s security posture | * [http://us-cert.cisa.gov/sites/default/files/FactSheets/NCCIC%20ICS_FactSheet_CSET_S508C.pdf The Cyber Security Evaluation Tool (CSET®) | National Cybersecurity and Communications Integration Center] ...provides a systematic, disciplined, and repeatable approach for evaluating an organization’s security posture | ||
| − | |||
* [[Watch me Build a Cybersecurity Startup]] | [[Creatives#Siraj Raval|Siraj Raval]] | * [[Watch me Build a Cybersecurity Startup]] | [[Creatives#Siraj Raval|Siraj Raval]] | ||
| Line 208: | Line 207: | ||
<b>Leveraging Machine Learning for Fraud Analytics (Cloud Next '18) | <b>Leveraging Machine Learning for Fraud Analytics (Cloud Next '18) | ||
</b><br>We will showcase how we can build advance accelerators for Fraud Analytics solutions leveraging [[Google]] Stack. We will demonstrate how these accelerators fill the gaps that exists within other Fraud Analytics solutions currently available in the market today and how it can offer several benefits including real-time processing, increased accuracy, scalable database and high performance. MLAI102 Event schedule http://g.co/next18 Watch more Machine Learning & AI sessions here → http://bit.ly/2zGKfcg Next ‘18 All Sessions playlist http://bit.ly/Allsessions Subscribe to the [[Google]] Cloud channel! → http://bit.ly/NextSub | </b><br>We will showcase how we can build advance accelerators for Fraud Analytics solutions leveraging [[Google]] Stack. We will demonstrate how these accelerators fill the gaps that exists within other Fraud Analytics solutions currently available in the market today and how it can offer several benefits including real-time processing, increased accuracy, scalable database and high performance. MLAI102 Event schedule http://g.co/next18 Watch more Machine Learning & AI sessions here → http://bit.ly/2zGKfcg Next ‘18 All Sessions playlist http://bit.ly/Allsessions Subscribe to the [[Google]] Cloud channel! → http://bit.ly/NextSub | ||
| + | |} | ||
| + | |}<!-- B --> | ||
| + | |||
| + | |||
| + | = <span id="MITRE ATT&CK™"></span>MITRE ATT&CK™ = | ||
| + | [http://www.youtube.com/results?search_query=MITRE+ATT&CK+threat+cybersecurity+securitydata+center+security+artificial+intelligence+ai Youtube search...] | ||
| + | [http://www.google.com/search?q=MITRE+ATT&CK+threat+cybersecurity+securitydata+center+security+artificial+intelligence+ai ...Google search] | ||
| + | |||
| + | * [http://mitre-attack.github.io/attack-navigator/enterprise/ ATT&CK™ Navigator |] [http://www.mitre.org/ MITRE] ...measure your threat detection | ||
| + | * [http://attack.mitre.org/ ATT&CK™ Homepage |] [http://www.mitre.org/ MITRE] | ||
| + | * [http://attack.mitre.org/resources/ ATT&CK™ Resources |] [http://www.mitre.org/ MITRE] | ||
| + | |||
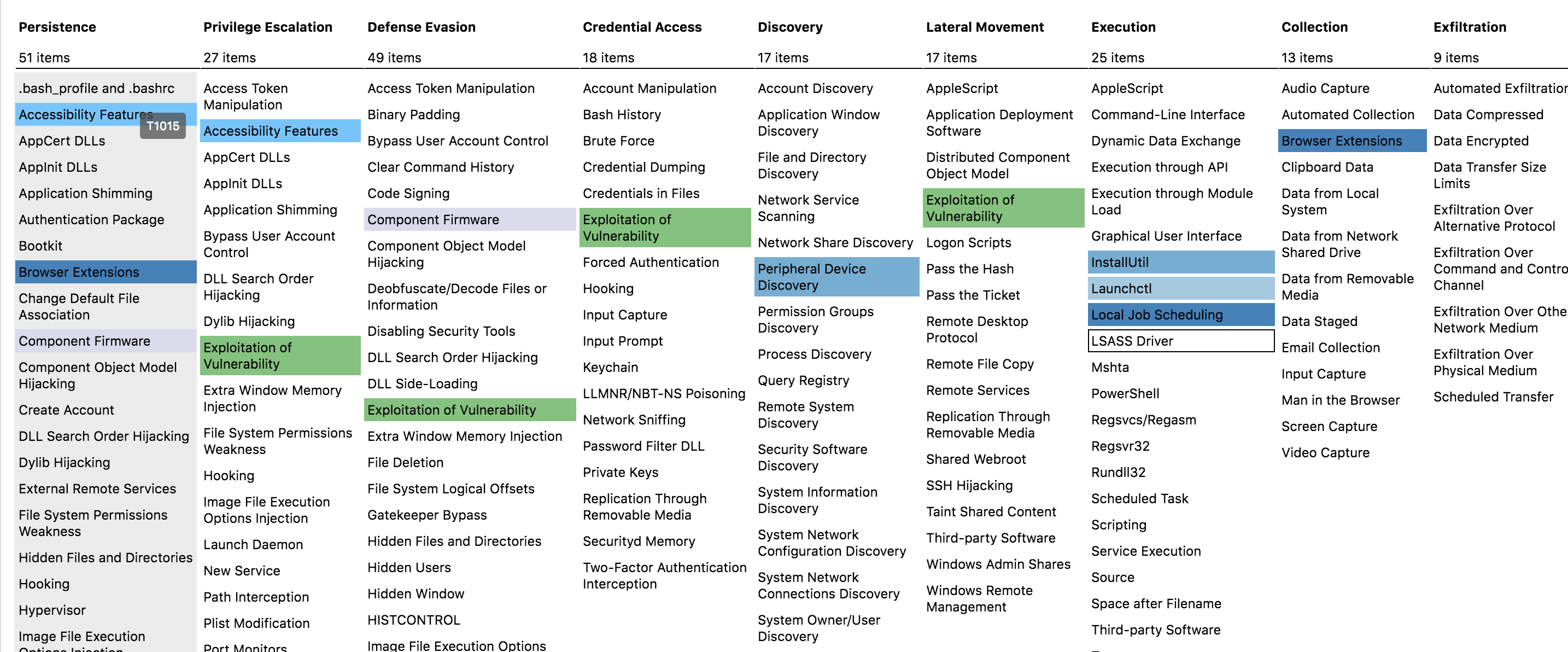
| + | knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community. | ||
| + | |||
| + | <img src="http://attack.mitre.org/theme/images/navigatorss.png" width="1000"> | ||
| + | |||
| + | {|<!-- T --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>bkfwMADar0M</youtube> | ||
| + | <b>Putting MITRE ATT&CK™ into Action with What You Have, Where You Are presented by Katie Nickels | ||
| + | </b><br>MITRE ATT&CK™ has become widely adopted in the community as a way to frame adversary behaviors and improve defenses. But how can you use it for your team with what you have, where you are? Katie Nickels will break down the ATT&CK knowledge base so you understand how you can put it into action. She will explain the philosophy and approach behind ATT&CK, then dive into how you can use it, whether you’re a one-person shop or an advanced security operations center. Katie will cover how you can use ATT&CK for detection, threat intelligence, assessments, and red teaming, with a focus on actionable takeaways to help your team move toward a threat-informed defense. Speaker: Katie Nickels, ATT&CK Threat Intelligence Lead at The MITRE Corporation Katie Nickels is the ATT&CK Threat Intelligence Lead at The MITRE Corporation, where she focuses on applying cyber threat intelligence to ATT&CK and sharing why that’s useful. She has worked in Security Operations Centers and cyber threat intelligence for nearly a decade, hailing from a liberal arts background with degrees from Smith College and Georgetown University. With more than a dozen publications to her name, Katie has shared her expertise with presentations at BSides LV, the FIRST CTI Symposium, multiple SANS Summits, and other events. She is also a SANS instructor for FOR578: Cyber Threat Intelligence and was a member of the 2019 SANS CTI Summit Advisory Board. Katie was the 2018 recipient of the President's Award from the Women's Society of Cyberjutsu and serves as the Program Manager for the Cyberjutsu Girls Academy. | ||
| + | |} | ||
| + | |<!-- M --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>EsvUUCrbhIE</youtube> | ||
| + | <b>MITRE ATT&CK™ Framework | ||
| + | </b><br>MITRE ATT&CK™ is a knowledge base that helps model cyber adversaries' tactics and techniques – and then shows how to detect or stop them. Updated February 5, 2019 | ||
| + | |} | ||
| + | |}<!-- B --> | ||
| + | {|<!-- T --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>CV37tSThUNg</youtube> | ||
| + | <b>Building MITRE ATT&CK Technique Detection into Your Security Monitoring Environment | ||
| + | </b><br>Randy Franklin Smith of Ultimate Windows Security and Brian Coulson of LogRhythm introduce viewers to MITRE ATT&CK, which is a knowledge base that features adversary tactics and techniques. In this webinar, you will: - Learn about various ways to use ATT&CK, specifically in relation to designing, enhancing, assessing, and maintaining your security monitoring efforts. - Hear Brian discuss LogRhythm Labs’ project that includes aligning the ATT&CK matrix with log sources. - Walk through an example of the MITRE attack process from start to finish while focusing on rule development and alignment in the LogRhythm NextGen SIEM Platform. | ||
| + | |} | ||
| + | |<!-- M --> | ||
| + | | valign="top" | | ||
| + | {| class="wikitable" style="width: 550px;" | ||
| + | || | ||
| + | <youtube>cmOAKLQnybk</youtube> | ||
| + | <b>Mapping Your Network to Mitre ATT&CK to Visualize Threats, Logging, and Detection w/ Wade Wells | ||
| + | </b><br>Wild West Hackin' Fest Find out about upcoming Hackin' Casts, training, and in-person & virtual infosec conferences at https://www.wildwesthackinfest.com 0:00 - Hotel California | ||
| + | 0:42 - The Mitre Attack Map 3:21 - Three Tools 3:52 - OK But Why? 4:40 - So Hot Right Now | ||
| + | 5:26 - Challenge Accepted 7:00 - Mitre ATT&CK Navigator 9:14 - DeTT&CT 18:23 - My Network's Setup Example 20:34 - Atomic Red Team 23:43 - End Credits 24:12 - Q&A Extended Edition Using open-source tools, Wade will describe how to map, test and display your network logging/detections to the Mitre ATT&CK framework while also comparing it to threat actors TTP’s. | ||
|} | |} | ||
|}<!-- B --> | |}<!-- B --> | ||
= Data Center Security = | = Data Center Security = | ||
| + | [http://www.youtube.com/results?search_query=data+center+security+artificial+intelligence+ai Youtube search...] | ||
| + | [http://www.google.com/search?q=data+center+security+artificial+intelligence+ai ...Google search] | ||
{|<!-- T --> | {|<!-- T --> | ||
Revision as of 08:17, 8 October 2020
Youtube search... ...Google search
- Case Studies
- Capabilities
- Cybersecurity References
- Offense - Adversarial Threats/Attacks
- Cybersecurity Frameworks, Architectures & Roadmaps
- Cybersecurity Companies/Products
- Cybersecurity: Evaluating & Selling
- (Artificial) Immune System
- 5G Security
- AIOps / MLOps
- Cybersecurity - Gaming
- Useful Models ...find outliers:
- Detecting Malicious Requests with Keras & TensorFlow | Adam Kusey - Medium
- Best security software: How 12 cutting-edge tools tackle today's threats | CSO
- Graph
- Intelligence Advanced Research Projects Activity (IARPA)Is Trying Keep Adversaries From Corrupting AI Tools ... Could cyber adversaries be training the government’s artificial intelligence tools to fail? | Jack Corrigan - Nextgov
- TrojAI - Office of the Director of National Intelligence Office: Intelligence Advanced Research Projects Activity FedBizOpps.gov predict whether AI systems have been corrupted through so-called “Trojan attacks.”
- Adversarial Attacks on Graph Convolutional Network (GCN), Graph Neural Networks (Graph Nets), Geometric Deep Learning
- Breaking Down the Tencent 2018 Cybersecurity Report
- Chronicle combines all the best parts of Google and X culture
- Fraud and Anomaly Detection | Chris Nicholson - A.I. Wiki pathmind
- The Cyber Security Evaluation Tool (CSET®) | National Cybersecurity and Communications Integration Center ...provides a systematic, disciplined, and repeatable approach for evaluating an organization’s security posture
- Watch me Build a Cybersecurity Startup | Siraj Raval
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Fraud Detection
- Introduction to Fraud Detection Systems | Miguel Gonzalez-Fierro, Microsoft
- AI for Health Insurance Fraud Detection – Current Applications | Niccolo Mejia
|
|
|
|
MITRE ATT&CK™
Youtube search... ...Google search
- ATT&CK™ Navigator | MITRE ...measure your threat detection
- ATT&CK™ Homepage | MITRE
- ATT&CK™ Resources | MITRE
knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
|
|
|
|
Data Center Security
Youtube search... ...Google search
|
|
|
|
|
|