Blockchain
Youtube search... ...Google search
- Case Studies
- Decentralized: Federated & Distributed
- Directed Acyclic Graph (DAG)
- Metaverse
- Privacy
- OpenMined
- Non-Fungible Token (NFT)
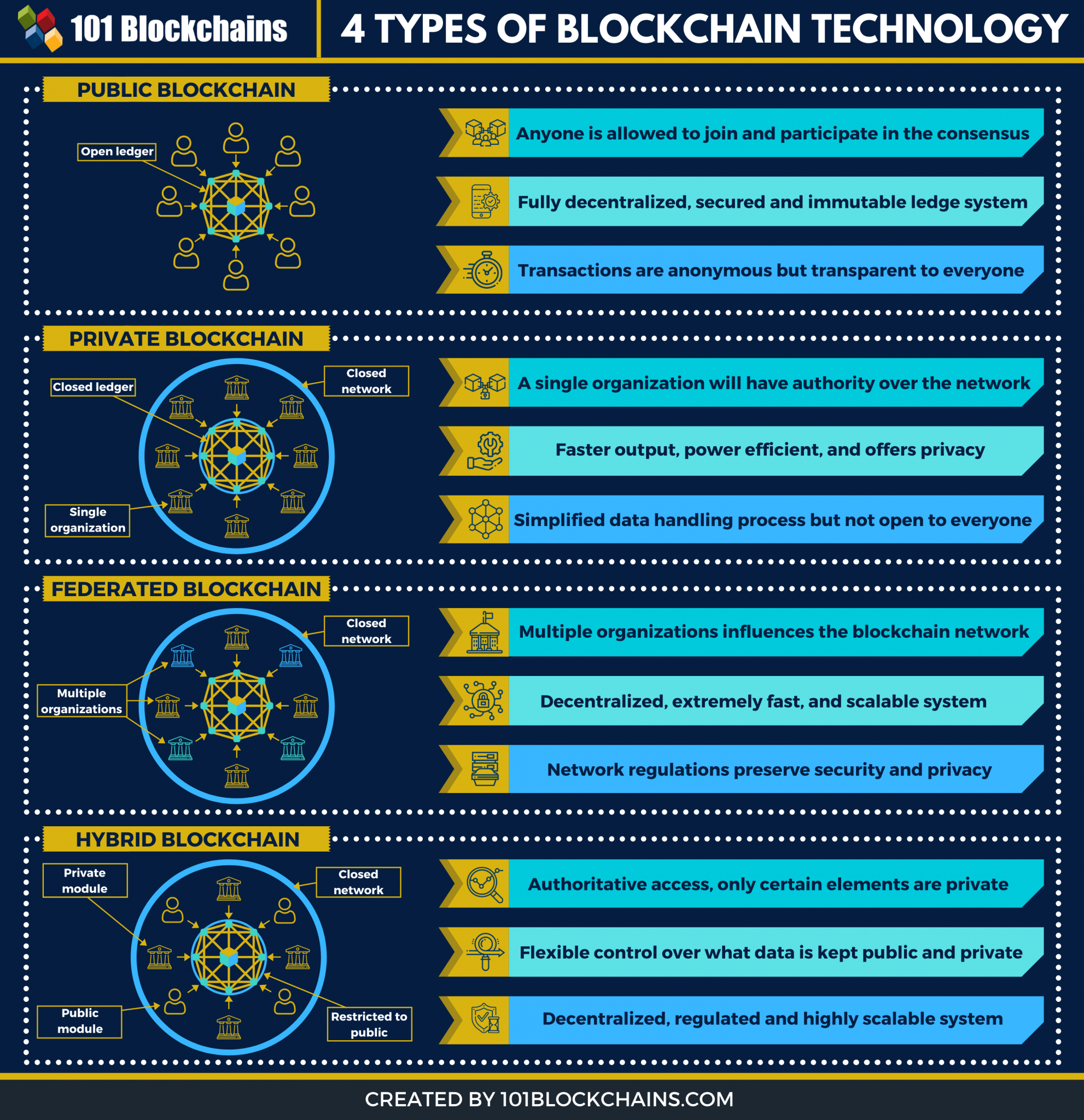
- 4 Different Types of Blockchain Technology & Networks | 101 Bloackchains
- Decentralized Autonomous Organization (DAO) | Wikipedia
- Fork (blockchain)
- Bill Gates Sounds Alarm On Bitcoin's Energy Consumption–Here's Why Crypto Is Bad For Climate Change | Jonathan Ponciano - Forbes ... According to Digiconomist, one bitcoin transaction requires about 707.6 kilowatt-hours of electrical energy, the amount of energy the average U.S. household consumes in 24 days.
A blockchain is a growing list of records, called blocks, that are linked together using cryptography. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree). The timestamp proves that the transaction data existed when the block was published in order to get into its hash. As blocks each contain information about the block previous to it, they form a chain, with each additional block reinforcing the ones before it. Therefore, blockchains are resistant to modification of their data because once recorded, the data in any given block cannot be altered retroactively without altering all subsequent blocks. Blockchains are typically managed by a peer-to-peer network for use as a publicly distributed ledger, where nodes collectively adhere to a protocol to communicate and validate new blocks. Although blockchain records are not unalterable as forks are possible, blockchains may be considered secure by design and exemplify a distributed computing system with high Byzantine fault tolerance.Wikipedia
Contents
[hide]How Does It Work?
Behind blockchains & cryptocurrencies
|
|
- If you are interested in playing with this on your own | Anders Brownworth
- The code that runs this demo is also on GitHub | Anders Brownworth
|
|
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published in 2001. They are built using the Merkle–Damgård construction, from a one-way compression function itself built using the Davies–Meyer structure from a specialized block cipher. ..The SHA-2 family consists of six hash functions with digests (hash values) that are 224, 256, 384 or 512 bits... .SHA-2 was first published by the National Institute of Standards and Technology (NIST) as a U.S. federal standard (FIPS). The SHA-2 family of algorithms are patented in US patent 6829355. The United States has released the patent under a royalty-free license. | Wikipedia
Introduction
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone. Bitcoin: A Peer-to-Peer Electronic Cash System | Satoshi Nakamoto - bitcoin.org
Programming
Uses
Youtube search... ...Google search
- Gaming
- Agriculture
- Healthcare
- Law
- Banking
- Real Estate
- ... other uses of blockchain: cryptocurrencies, smart contracts, energy trading, supply chain, anti-counterfeiting, domain names, decentralized voting, proof of existence and
Supply Chain
Blockchain use cases for supply chain include immutability into the provenance of goods, the elimination of reconciliation pain across multiple parties and the real-time visibility to perform track and trace analysis, assess risks and accelerate physical and financial supply chains. Blockchain for supply chain management: use cases and applications | r3
Distributed Ledger
A distributed ledger is a database that is consensually shared and synchronized across multiple sites, institutions, or geographies, accessible by multiple people. ... Underlying distributed ledgers is the same technology that is used by blockchain, which is the technology that is used by bitcoin.