Difference between revisions of "Telecommunications"
m |
m |
||
| Line 5: | Line 5: | ||
|description=Helpful resources for your journey with artificial intelligence; videos, articles, techniques, courses, profiles, and tools | |description=Helpful resources for your journey with artificial intelligence; videos, articles, techniques, courses, profiles, and tools | ||
}} | }} | ||
| − | [ | + | [https://www.youtube.com/results?search_query=telco+telecom+telecomunications+artificial+intelligence+deep+learning Youtube search...] |
| − | [ | + | [https://www.google.com/search?q=telco+telecom+telecommunication+deep+machine+learning+ML ...Google search] |
* [[Case Studies]] | * [[Case Studies]] | ||
| Line 14: | Line 14: | ||
* [[Time#Global Positioning System (GPS)|Global Positioning System (GPS)]] | * [[Time#Global Positioning System (GPS)|Global Positioning System (GPS)]] | ||
** [[Time#Software-defined Global Navigation Satellite Systems (GNSS)|Software-defined Global Navigation Satellite Systems (GNSS)]] | ** [[Time#Software-defined Global Navigation Satellite Systems (GNSS)|Software-defined Global Navigation Satellite Systems (GNSS)]] | ||
| − | * [ | + | * [https://www.ericsson.com/en/news/2019/10/ericsson-ai-to-boost-ran Ericsson launches unique AI functionality to boost radio access networks] |
| − | * [ | + | * [https://www.deepsig.io/ Deepsig] pioneering the application of deep learning to wireless |
| − | * [ | + | * [https://www.digitalistmag.com/digital-economy/2018/07/18/how-machine-learning-is-creating-new-opportunities-in-telecommunications-industry-06179697 How Machine Learning Is Creating New Opportunities In The Telecommunications Industry | Julie Stoughton - Digitalist Magazine] |
| − | * [ | + | * [https://medium.com/activewizards-machine-learning-company/top-10-data-science-use-cases-in-telecom-e9c334d42616 Top 10 Data Science Use cases in Telecom | Igor Bobriakov - Medium] |
<youtube>Wsj45HW8htA</youtube> | <youtube>Wsj45HW8htA</youtube> | ||
| Line 28: | Line 28: | ||
== Cognitive Radio (CR) / Software-defined radio (SDR) == | == Cognitive Radio (CR) / Software-defined radio (SDR) == | ||
| − | * [ | + | * [https://en.wikipedia.org/wiki/Software-defined_radio Wikipedia] |
| − | Software-defined radio (SDR) is a radio communication system where components that have been traditionally implemented in hardware (e.g. mixers, filters, amplifiers, modulators/demodulators, detectors, etc.) are instead implemented by means of software on a personal computer or embedded system. Software radios have significant utility for the military and cell phone services, both of which must serve a wide variety of changing radio protocols in real time. In the long term, software-defined radios are to become the dominant technology in radio communications. SDRs, along with [ | + | Software-defined radio (SDR) is a radio communication system where components that have been traditionally implemented in hardware (e.g. mixers, filters, amplifiers, modulators/demodulators, detectors, etc.) are instead implemented by means of software on a personal computer or embedded system. Software radios have significant utility for the military and cell phone services, both of which must serve a wide variety of changing radio protocols in real time. In the long term, software-defined radios are to become the dominant technology in radio communications. SDRs, along with [https://en.wikipedia.org/wiki/Reconfigurable_antenna software defined antennas] are the enablers of the cognitive radio. |
<youtube>-10nYoNOgTw</youtube> | <youtube>-10nYoNOgTw</youtube> | ||
<youtube>09eXRHf6glA</youtube> | <youtube>09eXRHf6glA</youtube> | ||
| − | === [ | + | === [https://www.gnuradio.org/ GNU Radio] === |
| − | * [ | + | * [https://en.wikipedia.org/wiki/GNU_Radio GNU Radio | Wikipedia] |
| − | * [ | + | * [https://www.gnuradio.org/ GNU Radio.org] |
is a free & open-source software development toolkit that provides signal processing blocks to implement software radios. It can be used with readily-available low-cost external RF hardware to create software-defined radios, or without hardware in a simulation-like environment. | is a free & open-source software development toolkit that provides signal processing blocks to implement software radios. It can be used with readily-available low-cost external RF hardware to create software-defined radios, or without hardware in a simulation-like environment. | ||
| Line 47: | Line 47: | ||
<youtube>RuJ0EOcN6dk</youtube> | <youtube>RuJ0EOcN6dk</youtube> | ||
| − | === [ | + | === [https://deepwavedigital.com/ Deepwave Digital Systems] === |
| − | Enabling deep learning and AI at the edge of wireless systems. GPUs are extremely well suited for processes that are highly parallel. The Fast Fourier Transform (FFT) is one of the most common techniques in signal processing and happens to be a highly parallel algorithm. In this blog post the Deepwave team walks you though how to leverage the embedded GPU built into the AIR-T to perform high-speed FFTs without the computational bottleneck of a CPU and without having to experience the long development cycle associated with writing VHDL code for FPGAs. By leveraging the GPU on the AIR-T, you get the best of both worlds: fast development time and high speed processing. A familiar tool to anyone working in the wireless domain, GNU Radio allows signal processing experts to tie together blocks of functionality using an intuitive GUI. Many of the “in the weeds” details regarding the software implementation are well abstracted so the user can focus on the algorithm instead.Once an algorithm has been optimized (or a pre-trained algorithm has been downloaded by a 3rd party), the user will reference it in Deepwave’s [ | + | Enabling deep learning and AI at the edge of wireless systems. GPUs are extremely well suited for processes that are highly parallel. The Fast Fourier Transform (FFT) is one of the most common techniques in signal processing and happens to be a highly parallel algorithm. In this blog post the Deepwave team walks you though how to leverage the embedded GPU built into the AIR-T to perform high-speed FFTs without the computational bottleneck of a CPU and without having to experience the long development cycle associated with writing VHDL code for FPGAs. By leveraging the GPU on the AIR-T, you get the best of both worlds: fast development time and high speed processing. A familiar tool to anyone working in the wireless domain, GNU Radio allows signal processing experts to tie together blocks of functionality using an intuitive GUI. Many of the “in the weeds” details regarding the software implementation are well abstracted so the user can focus on the algorithm instead.Once an algorithm has been optimized (or a pre-trained algorithm has been downloaded by a 3rd party), the user will reference it in Deepwave’s [https://essentials.news/ai/general/article/gr-wavelearner-45fe89566f GR-WAVELEARNER] software that provides a TensorRT Inference block for GNU Radio Companion (GRC) |
| − | + | https://deepwavedigital.com/wp-content/uploads/2019/09/fft_gif.gif | |
<youtube>uGAGhIJLdd4</youtube> | <youtube>uGAGhIJLdd4</youtube> | ||
| Line 58: | Line 58: | ||
<youtube>sj0-QRCQ3Hw</youtube> | <youtube>sj0-QRCQ3Hw</youtube> | ||
| − | <img src=" | + | <img src="https://deepwavedigital.com/wp-content/uploads/2019/06/ezgif.com-webp-to-png-1-1.png" width="1000" height="1000"> |
== Machine learning solving practical problems in Communications == | == Machine learning solving practical problems in Communications == | ||
| Line 68: | Line 68: | ||
== <span id="Physical Layer Security (PLS)"></span>Physical Layer Security (PLS) == | == <span id="Physical Layer Security (PLS)"></span>Physical Layer Security (PLS) == | ||
| − | [ | + | [https://www.youtube.com/results?search_query=Physical+layer+security+PLS+artificial+intelligence+deep+learning Youtube search...] |
| − | [ | + | [https://www.google.com/search?q=Physical+layer+security+PLS+artificial+intelligence+deep+learning ...Google search] |
* [[Cybersecurity]] | * [[Cybersecurity]] | ||
* [[Signal Processing]] | * [[Signal Processing]] | ||
| − | Physical layer security (PLS) has emerged as a new concept and powerful alternative that can complement and may even replace encryption-based approaches, which entail many hurdles and practical problems for future wireless systems. The basic idea of PLS is to exploit the characteristics of the wireless channel and its impairments including noise, fading, interference, dispersion, diversity, etc. in order to ensure the ability of the intended user to successfully perform data decoding while preventing eavesdroppers from doing so. Thus, the main design goal of PLS is to increase the performance difference between the link of the legitimate receiver and that of the eavesdropper by using well-designed transmission schemes. [ | + | Physical layer security (PLS) has emerged as a new concept and powerful alternative that can complement and may even replace encryption-based approaches, which entail many hurdles and practical problems for future wireless systems. The basic idea of PLS is to exploit the characteristics of the wireless channel and its impairments including noise, fading, interference, dispersion, diversity, etc. in order to ensure the ability of the intended user to successfully perform data decoding while preventing eavesdroppers from doing so. Thus, the main design goal of PLS is to increase the performance difference between the link of the legitimate receiver and that of the eavesdropper by using well-designed transmission schemes. [https://arxiv.org/pdf/1905.05064.pdf Physical Layer Security for Downlink NOMA: Requirements, Merits, Challenges, and Recommendations | H. Furqan, J. Hamamreh, and H. Arslan] |
<youtube>_0ZyeF11pMY</youtube> | <youtube>_0ZyeF11pMY</youtube> | ||
| Line 79: | Line 79: | ||
=== <span id="Waveform"></span>Waveform === | === <span id="Waveform"></span>Waveform === | ||
| − | [ | + | [https://www.youtube.com/results?search_query=waveform+wireless+spectrum+Physical+layer+security+PLS+artificial+intelligence+deep+learning Youtube search...] |
| − | [ | + | [https://www.google.com/search?q=waveform+wireless+spectrum+Physical+layer+security+PLS+artificial+intelligence+deep+learning ...Google search] |
<youtube>gYFSRCJRzG4</youtube> | <youtube>gYFSRCJRzG4</youtube> | ||
| Line 86: | Line 86: | ||
= <span id="5G"></span>5G = | = <span id="5G"></span>5G = | ||
| − | [ | + | [https://www.youtube.com/results?search_query=5G+deep+machine+learning+ML+artificial+intelligence+ai YouTube search...] |
| − | [ | + | [https://www.google.com/search?q=5G+deep+machine+learning+ML+artificial+intelligence+ai ...Google search] |
* [[Internet of Things (IoT)]] | * [[Internet of Things (IoT)]] | ||
| − | * [ | + | * [https://www.3gpp.org/dynareport/SpecList.htm?release=Rel-15&tech=4 3rd Generation Partnership Project (3GPP)] ...unites [Seven] telecommunications standard development organizations: ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC |
| − | * [ | + | * [https://www.ietf.org/blog/5g-and-internet-technology/ Internet Engineering Taskforce (IETF)] |
| − | * [ | + | * [https://www.nist.gov/topics/advanced-communications/what-5g What is 5G? | NIST] |
| − | * [ | + | * [https://www.etsi.org/technologies/nfv European Telecommunications Standards Institute (ETSI) ISG Network Functions Virtualisation (NFV) - ETSI Industry Specification Group] |
| − | * [ | + | * [https://en.wikipedia.org/wiki/China_Global_Television_Network China Global Television Network (CGTN) | Wikipedia] |
| − | * [ | + | * [https://www.prnewswire.com/ae/news-releases/5g-cloud-ai-huawei-works-with-carriers-to-power-new-ict-infrastructure-846412775.html 5G + Cloud + AI: Huawei Works with Carriers to Power New ICT Infrastructure | Huawei - PR Newswire] |
| − | * [ | + | * [https://www.afcea.org/site/ Armed Forces Communications and Electronics Association] ...communications, information technology, intelligence and security |
| − | * [ | + | * [https://en.wikipedia.org/wiki/MIMO MIMO | Wikipedia] |
{|<!-- T --> | {|<!-- T --> | ||
| Line 130: | Line 130: | ||
<youtube>InPzlUE5Qck</youtube> | <youtube>InPzlUE5Qck</youtube> | ||
<b>Why [[Government Services#China|China]] can take a lead in 5G and AI technology application | <b>Why [[Government Services#China|China]] can take a lead in 5G and AI technology application | ||
| − | </b><br>[[Government Services#China|China]] is among the world’s first countries to apply 5G to business services. [[Government Services#China|China]]’s telecommunications guides the global 5G-technology trend. An open [[Government Services#China|China]] is becoming the “playground” for global AI businesses and a key landmark for a joint exploration of AI’s direction of end development. Check out this video and have a look at why [[Government Services#China|China]] can take a lead in 5G and AI technology application. Subscribe to us on YouTube: | + | </b><br>[[Government Services#China|China]] is among the world’s first countries to apply 5G to business services. [[Government Services#China|China]]’s telecommunications guides the global 5G-technology trend. An open [[Government Services#China|China]] is becoming the “playground” for global AI businesses and a key landmark for a joint exploration of AI’s direction of end development. Check out this video and have a look at why [[Government Services#China|China]] can take a lead in 5G and AI technology application. Subscribe to us on YouTube: https://goo.gl/lP12gA |
|} | |} | ||
|}<!-- B --> | |}<!-- B --> | ||
== <span id="5G Security"></span>5G Security == | == <span id="5G Security"></span>5G Security == | ||
| − | [ | + | [https://www.youtube.com/results?search_query=5G+security+deep+machine+learning+ML+artificial+intelligence+ai YouTube search...] |
| − | [ | + | [https://www.google.com/search?q=5G+security+deep+machine+learning+ML+artificial+intelligence+ai ...Google search] |
* [[Cybersecurity]] | * [[Cybersecurity]] | ||
| − | * [ | + | * [https://owasp.org/www-community/Application_Threat_Modeling Application Threat Modeling OWASP.org] |
| − | Three-step approach to reach a high level of intelligent security management. [ | + | Three-step approach to reach a high level of intelligent security management. [https://www.ericsson.com/en/blog/2020/10/how-to-master-e2e-network-security-when-introducing-5g-core How to master E2E network security when introducing 5G core | Kari-Pekka Perttula - Ericsson] |
* Dynamic: Introduce automated security policy configuration and compliance monitoring | * Dynamic: Introduce automated security policy configuration and compliance monitoring | ||
| Line 148: | Line 148: | ||
* Intelligent: Repeatable, adaptive and holistic security management with threat intelligence. This provides end-to-end visibility for business-related security risks, and actions can be directed via automated workflows to mitigate risks faster. | * Intelligent: Repeatable, adaptive and holistic security management with threat intelligence. This provides end-to-end visibility for business-related security risks, and actions can be directed via automated workflows to mitigate risks faster. | ||
| − | [ | + | [https://en.wikipedia.org/wiki/Threat_model Threat Model:] [https://en.wikipedia.org/wiki/STRIDE_(security) STRIDE | Wikipedia] The threats are: |
| − | * [ | + | * [https://en.wikipedia.org/wiki/Spoofing_attack '''S'''poofing] |
| − | * [ | + | * [https://en.wikipedia.org/wiki/Tampering_(crime) '''T'''ampering] |
| − | * [ | + | * [https://en.wikipedia.org/wiki/Non-repudiation '''R'''epudiation] |
* '''I'''nformation disclosure ([https://en.wikipedia.org/wiki/Information_privacy|privacy breach] or [https://en.wikipedia.org/wiki/Data_breach data leak]) | * '''I'''nformation disclosure ([https://en.wikipedia.org/wiki/Information_privacy|privacy breach] or [https://en.wikipedia.org/wiki/Data_breach data leak]) | ||
| − | * [ | + | * [https://en.wikipedia.org/wiki/Denial-of-service_attack '''D'''enial of service] |
| − | * [ | + | * [https://en.wikipedia.org/wiki/Privilege_escalation '''E'''levation of privilege]] |
{|<!-- T --> | {|<!-- T --> | ||
| Line 214: | Line 214: | ||
== <span id="5G Testing"></span>5G Testing == | == <span id="5G Testing"></span>5G Testing == | ||
| − | [ | + | [https://www.youtube.com/results?search_query=5G+testing+deep+machine+learning+ML+artificial+intelligence+ai YouTube search...] |
| − | [ | + | [https://www.google.com/search?q=5G+testing+deep+machine+learning+ML+artificial+intelligence+ai ...Google search] |
* [[Algorithm_Administration#Model_Monitoring|Model_Monitoring]] | * [[Algorithm_Administration#Model_Monitoring|Model_Monitoring]] | ||
| − | * [ | + | * [https://www.defense.gov/Explore/News/Article/Article/2378047/dod-kicks-off-worlds-largest-dual-use-5g-testing-effort/Experimentation DOD Kicks Off World’s Largest Dual-Use 5G Testing Effort | C. Todd Lopez -] [[Defense| DOD News]] ...AT&T, Booz Allen Hamilton, Deloitte Consulting LLP, Ericsson, Federated Wireless, GBL System Corp., General Dynamics Mission Systems, Inc., GE Research, Key Bridge Wireless LLC, KPMG LLP, Nokia, Oceus Networks, Scientific Research Corporation, Shared Spectrum Company and Vectrus Mission Solutions Corporation. |
{|<!-- T --> | {|<!-- T --> | ||
| Line 239: | Line 239: | ||
= <span id="Virtualization - Dynamic Spectrum Sharing (DSS)"></span>Virtualization - Dynamic Spectrum Sharing (DSS) = | = <span id="Virtualization - Dynamic Spectrum Sharing (DSS)"></span>Virtualization - Dynamic Spectrum Sharing (DSS) = | ||
| − | [ | + | [https://www.youtube.com/results?search_query=defense+dod+darpa+disa+Virtualization+dynamic+Spectrum+sharing+artificial+intelligence+deep+machine+learning+ai Youtube search...] |
| − | [ | + | [https://www.google.com/search?q=defense+dod+darpa+disa+Virtualization+dynamic+Spectrum+sharing+artificial+intelligence+deep+machine+learning+ai ...Google search] |
| − | [ | + | [https://news.google.com/search?q=spectrum+AI ...Google News] |
* [[Telecommunications]] | * [[Telecommunications]] | ||
| Line 254: | Line 254: | ||
** [[Defense#US Defense Advanced Research Projects Agency (DARPA)|US Defense Advanced Research Projects Agency (DARPA)]] | ** [[Defense#US Defense Advanced Research Projects Agency (DARPA)|US Defense Advanced Research Projects Agency (DARPA)]] | ||
** [[Defense#US Defense Information Systems Agency (DISA)|Defense Information Systems Agency (DISA)]] | ** [[Defense#US Defense Information Systems Agency (DISA)|Defense Information Systems Agency (DISA)]] | ||
| − | * [ | + | * [https://www.lightwaveonline.com/network-design/high-speed-networks/article/16675796/how-to-know-if-youre-ready-to-deploy-a-dark-fiber-network How to Know if You’re Ready to Deploy a Dark Fiber Network | Rob Coenen - Lightwave] ...unused or under-utilized fiber infrastructure (including fibers, cabling, and repeaters) that was laid as part of a hedge against exponential growth in data use. |
Spectrum Sharing utilizes virtualization to partition optical spectrum | Spectrum Sharing utilizes virtualization to partition optical spectrum | ||
Revision as of 13:34, 4 January 2023
Youtube search... ...Google search
- Case Studies
- Global Positioning System (GPS)
- Ericsson launches unique AI functionality to boost radio access networks
- Deepsig pioneering the application of deep learning to wireless
- How Machine Learning Is Creating New Opportunities In The Telecommunications Industry | Julie Stoughton - Digitalist Magazine
- Top 10 Data Science Use cases in Telecom | Igor Bobriakov - Medium
Contents
Cognitive Radio (CR) / Software-defined radio (SDR)
Software-defined radio (SDR) is a radio communication system where components that have been traditionally implemented in hardware (e.g. mixers, filters, amplifiers, modulators/demodulators, detectors, etc.) are instead implemented by means of software on a personal computer or embedded system. Software radios have significant utility for the military and cell phone services, both of which must serve a wide variety of changing radio protocols in real time. In the long term, software-defined radios are to become the dominant technology in radio communications. SDRs, along with software defined antennas are the enablers of the cognitive radio.
GNU Radio
is a free & open-source software development toolkit that provides signal processing blocks to implement software radios. It can be used with readily-available low-cost external RF hardware to create software-defined radios, or without hardware in a simulation-like environment.
Deepwave Digital Systems
Enabling deep learning and AI at the edge of wireless systems. GPUs are extremely well suited for processes that are highly parallel. The Fast Fourier Transform (FFT) is one of the most common techniques in signal processing and happens to be a highly parallel algorithm. In this blog post the Deepwave team walks you though how to leverage the embedded GPU built into the AIR-T to perform high-speed FFTs without the computational bottleneck of a CPU and without having to experience the long development cycle associated with writing VHDL code for FPGAs. By leveraging the GPU on the AIR-T, you get the best of both worlds: fast development time and high speed processing. A familiar tool to anyone working in the wireless domain, GNU Radio allows signal processing experts to tie together blocks of functionality using an intuitive GUI. Many of the “in the weeds” details regarding the software implementation are well abstracted so the user can focus on the algorithm instead.Once an algorithm has been optimized (or a pre-trained algorithm has been downloaded by a 3rd party), the user will reference it in Deepwave’s GR-WAVELEARNER software that provides a TensorRT Inference block for GNU Radio Companion (GRC)
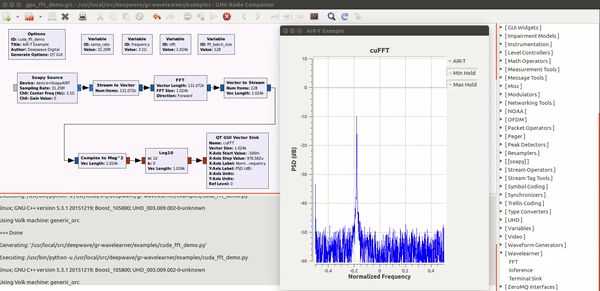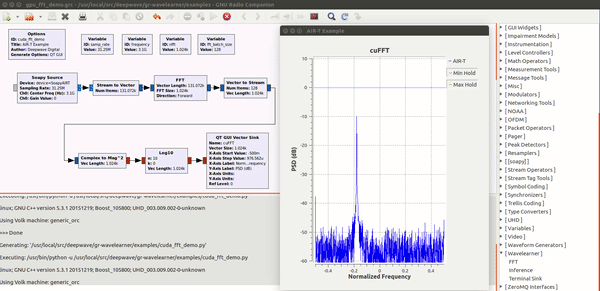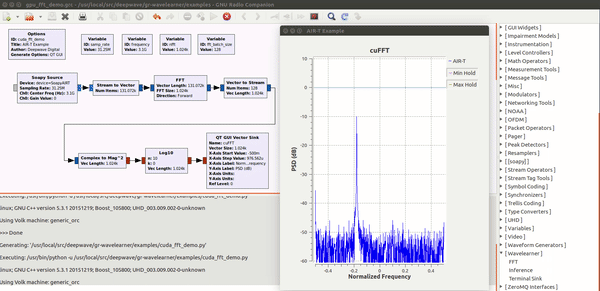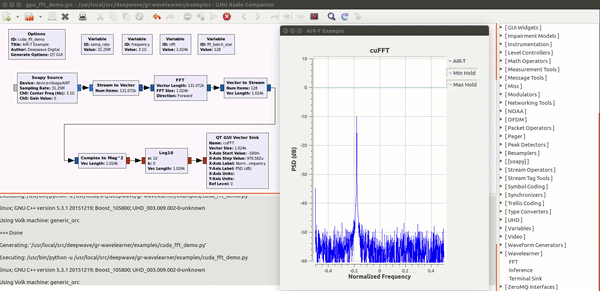

Machine learning solving practical problems in Communications
Physical Layer Security (PLS)
Youtube search... ...Google search
Physical layer security (PLS) has emerged as a new concept and powerful alternative that can complement and may even replace encryption-based approaches, which entail many hurdles and practical problems for future wireless systems. The basic idea of PLS is to exploit the characteristics of the wireless channel and its impairments including noise, fading, interference, dispersion, diversity, etc. in order to ensure the ability of the intended user to successfully perform data decoding while preventing eavesdroppers from doing so. Thus, the main design goal of PLS is to increase the performance difference between the link of the legitimate receiver and that of the eavesdropper by using well-designed transmission schemes. Physical Layer Security for Downlink NOMA: Requirements, Merits, Challenges, and Recommendations | H. Furqan, J. Hamamreh, and H. Arslan
Waveform
Youtube search... ...Google search
5G
YouTube search... ...Google search
- Internet of Things (IoT)
- 3rd Generation Partnership Project (3GPP) ...unites [Seven] telecommunications standard development organizations: ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC
- Internet Engineering Taskforce (IETF)
- What is 5G? | NIST
- European Telecommunications Standards Institute (ETSI) ISG Network Functions Virtualisation (NFV) - ETSI Industry Specification Group
- China Global Television Network (CGTN) | Wikipedia
- 5G + Cloud + AI: Huawei Works with Carriers to Power New ICT Infrastructure | Huawei - PR Newswire
- Armed Forces Communications and Electronics Association ...communications, information technology, intelligence and security
- MIMO | Wikipedia
|
|
|
|
5G Security
YouTube search... ...Google search
Three-step approach to reach a high level of intelligent security management. How to master E2E network security when introducing 5G core | Kari-Pekka Perttula - Ericsson
- Dynamic: Introduce automated security policy configuration and compliance monitoring
- Cognitive: Automated threat and vulnerability detection assisted with ML /AI
- Intelligent: Repeatable, adaptive and holistic security management with threat intelligence. This provides end-to-end visibility for business-related security risks, and actions can be directed via automated workflows to mitigate risks faster.
Threat Model: STRIDE | Wikipedia The threats are:
- Spoofing
- Tampering
- Repudiation
- Information disclosure (breach or data leak)
- Denial of service
- Elevation of privilege]
|
|
|
|
|
|
5G Testing
YouTube search... ...Google search
- Model_Monitoring
- DOD Kicks Off World’s Largest Dual-Use 5G Testing Effort | C. Todd Lopez - DOD News ...AT&T, Booz Allen Hamilton, Deloitte Consulting LLP, Ericsson, Federated Wireless, GBL System Corp., General Dynamics Mission Systems, Inc., GE Research, Key Bridge Wireless LLC, KPMG LLP, Nokia, Oceus Networks, Scientific Research Corporation, Shared Spectrum Company and Vectrus Mission Solutions Corporation.
|
|
Virtualization - Dynamic Spectrum Sharing (DSS)
Youtube search... ...Google search ...Google News
- Telecommunications
- Computer Networks
- Defense
- How to Know if You’re Ready to Deploy a Dark Fiber Network | Rob Coenen - Lightwave ...unused or under-utilized fiber infrastructure (including fibers, cabling, and repeaters) that was laid as part of a hedge against exponential growth in data use.
Spectrum Sharing utilizes virtualization to partition optical spectrum
|
|
|
|